Forbes reports that data breaches are becoming more frequent and expensive, with an average global cost of $4.45 million in 2023, a 15% increase since 2020. As a result, organizations are investing more in cybersecurity in response to a complex and evolving threat landscape. Application-level defects that expose system resources and user data account for more than 70% of exploited security vulnerabilities. Untrusted apps pose a unique challenge on Linux systems, as they often require extensive access to user files and kernel resources, which can be exploited if improperly isolated.
“We can only see a short distance ahead, but we can see plenty there that needs to be done,” as the famous computer scientist Alan Turing famously remarked. In light of the rapidly changing technological landscape, this quotation underscores the ongoing need for robust cybersecurity measures. The issue occurs because conventional Linux applications typically have shared access to system resources, such as the file system, process table, and network stack, as well as broad privileges. Due to the extensive attack surface created by this unfettered access, malicious or compromised software can more easily escalate privileges or steal sensitive data.
Modern Linux security uses sandboxing techniques, which isolate applications in controlled environments, to address this problem. One popular solution is Firejail, which builds lightweight sandboxes using seccomp-bpf filtering and Linux namespaces. These sandboxes limit access to files, network interfaces, and kernel resources, providing each application and its child with a private view of the system.
The method used by Firejail reduces overhead, eliminates the need for background daemons, and implements stringent access control rules to prevent thousands of popular applications from accessing private user information, such as encryption keys and passwords. Firejail is a crucial tool for protecting Linux desktops and servers in the current threat landscape, as it efficiently isolates processes, minimizing the potential harm from security breaches and protecting user privacy.
How Firejail Strengthens Linux Security
To separate and isolate application processes, Firejail utilizes several sophisticated Linux kernel features. Its foundation is Linux namespaces, which generate virtualized versions of system components, such as file system mounts, the process table, and the network stack. This implies that each sandboxed application runs in a separate, private environment that is hidden from and unavailable to other programs on the system.
By allowing only a restricted, secure set of operations for the application to execute, Firejail significantly lowers the attack surface when used in combination with seccomp-bpf, a kernel technology that filters and limits system calls. This multi-layered isolation mitigates risks, including privilege escalation and unauthorized system access. While remote work offers greater flexibility and boosts employee satisfaction and productivity, it also presents risks, including the use of unmanaged personal devices, unprotected home networks, and an increased susceptibility to phishing and social engineering attacks. To assist organizations in identifying vulnerabilities and implementing robust, multi-layered defenses aligned with Firejail’s sandboxing technique, Auxin Security offers expert Threat Modeling and Container Security consultations.
Easy Use with Predefined Profiles
Firejail’s ready-to-use security profiles for well-known Linux apps, such as Transmission, Chromium, VLC, and Firefox, are one of its advantages. Users can quickly sandbox software without requiring extensive technical knowledge thanks to these profiles, which adjust sandbox restrictions based on the typical behavior of each program. Simply prefixing the command with firejail will launch an application securely. Zero-trust security—an adaptive model that requires stringent identity verification and least-privilege access at every stage—emerges as a viable remedy.
Due to its simplicity of integration, Firejail is usable by both novice and experienced Linux users seeking robust security without requiring complex setup. With its DevSecOps services, Auxin Security helps businesses expedite secure development and deployment, ensuring that security seamlessly integrates with workflows, such as those enabled by Firejail profiles.
Keeping Your Privacy Safe with Access Control
Firejail uses Mandatory Access Control (MAC) mechanisms that enforce stringent file system access rules in addition to basic isolation. This keeps potentially dangerous or vulnerable apps from accessing private configuration files, encryption keys, and passwords, among other sensitive user data. Network-facing apps, for instance, are typically restricted to their download and configuration folders, which limits system exposure and significantly improves user privacy. Auxin Security helps businesses establish privacy-preserving policies and compliance controls that enhance Firejail’s MAC protections through advanced data science and Cloud Cybersecurity consulting.
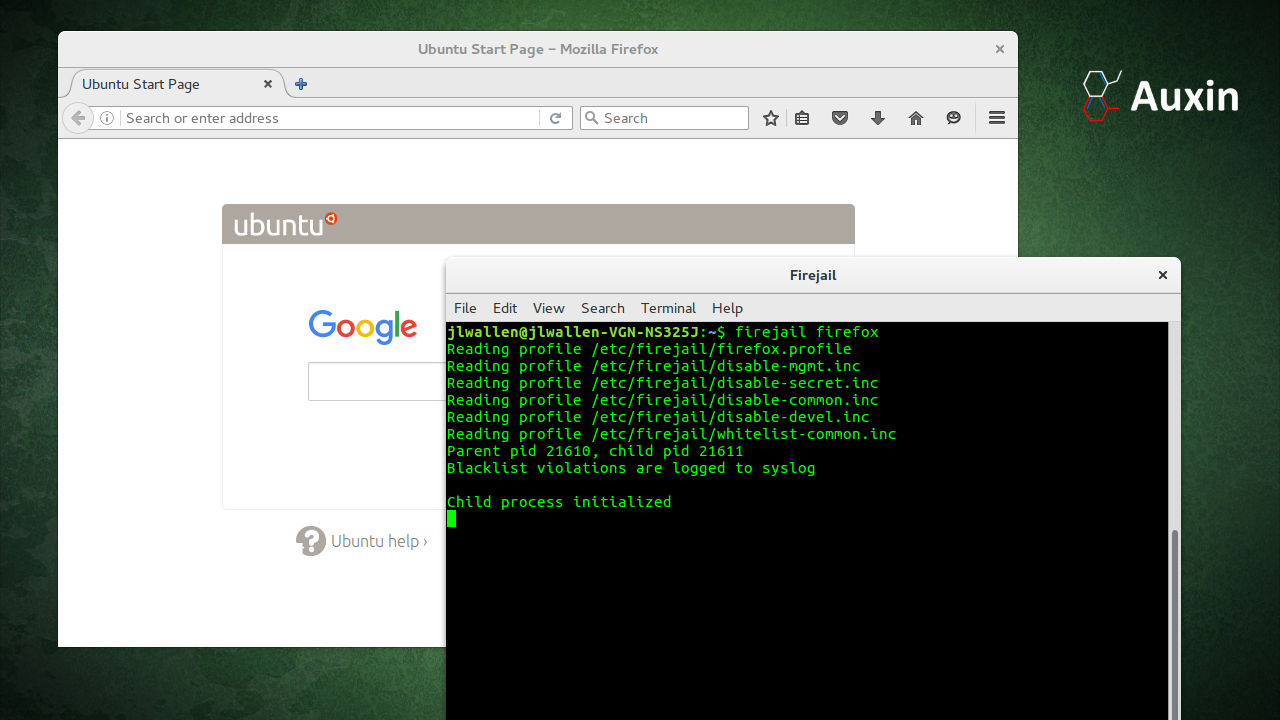
Lightweight Design and Community Support
Firejail is made with minimal external dependencies and is written in C to minimize performance overhead. It provides adequate security and doesn’t require complicated configurations or background daemons, unlike some sandboxing solutions. A dedicated group of Linux developers and security enthusiasts actively maintains Firejail, ensuring timely patches and ongoing enhancements.
It is adaptable to a wide variety of systems, including desktops and servers, thanks to its compatibility with Linux kernels starting with version 3.x. The knowledgeable Cloud Solutions Architects at Auxin Security assist businesses in integrating dependable and scalable cloud and on-premises infrastructures with practical, lightweight security tools, such as Firejail.
Extra Tools and Features for Better Protection
Firetools introduces a graphical user interface to the core sandbox, simplifying sandbox management. Firejail offers FDNS, a DNS-over-HTTPS proxy, for enhanced network privacy and security. It encrypts DNS queries using reliable, non-logging providers, thwarting common DNS-level attacks. To improve security and customization, users can also adjust sandbox controls, including options such as network namespace configurations, chroot environments, and resource limits (CPU and memory).
These extended environments are further protected by Auxin Security’s all-inclusive Cloud Cybersecurity and Container Security services, which ensure that such tools and configurations remain resilient against evolving cyber threats.
Keeping Linux Secure and Simple
Rising cyberattack expenses by 2025 underscore the need for Linux app sandboxing solutions, such as Firejail, to protect user data and system resources. Expert threat modeling and DevSecOps from Auxin Security support these initiatives, helping businesses successfully defend against evolving cyber threats.






