The Benefits of Incorporating Threat Modeling into Your SDLC
Threat modeling is a critical component of a robust cybersecurity strategy. It identifies potential security threats and vulnerabilities in an application or system before they are deployed. According to Gartner “As security and risk management development teams create security approaches, threat modeling should be viewed as an effective, long-term improvement tool”. Incorporating threat modeling into your software development lifecycle (SDLC) can help you identify and mitigate security risks early in development. In this post, we’ll discuss the benefits of incorporating threat modeling into your SDLC and how it can help improve the security of your applications and systems.
Threat modeling is a proactive approach to identifying and mitigating potential security risks and threats in software systems, applications, or networks. It is a structured process that helps organizations systematically analyze and understand the potential attack vectors, vulnerabilities, and impacts associated with their assets.
- Early Detection of Security Vulnerabilities: One of the primary benefits of incorporating it into your SDLC is the early detection of security vulnerabilities. By identifying and addressing potential security issues early in the development process, you can ensure they become more complex and costly to fix later.
- Cost Savings: This can help save costs for fixing security vulnerabilities post-deployment. When vulnerabilities are identified and addressed during development, it reduces the need for expensive post-deployment remediation efforts.
- Improved Security Posture: Incorporating it into your SDLC can help improve the overall security posture of your applications and systems. Proactively identifying and addressing security vulnerabilities reduces the likelihood of successful cyberattacks.
- Compliance Requirements: Many regulatory requirements mandate threat modeling in developing applications and systems. Using this in your SDLC can help you meet these compliance requirements and avoid penalties and fines.
- Improved Collaboration: This can also help improve collaboration between developers, security teams, and other stakeholders. By involving all stakeholders in the threat modeling process, you can identify potential security risks early and work together to address them.
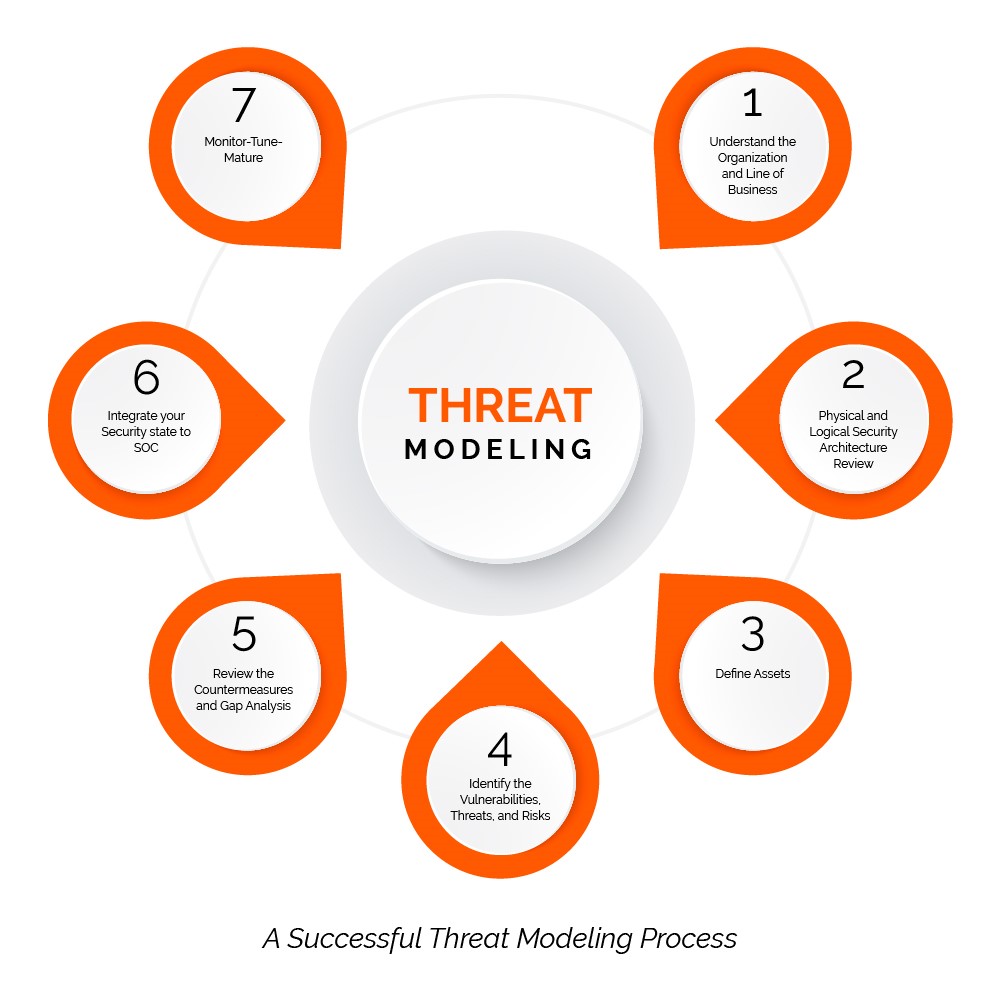
The Importance of Threat Modeling in Cybersecurity
Threat modeling is an essential process in cybersecurity that helps organizations identify and mitigate potential security threats and vulnerabilities in their systems and applications. It is a structured approach to understanding and addressing security risks before deployment.
Cyber-attacks are becoming increasingly cultivated and widespread in today’s threat landscape. This provides organizations with a proactive way to defend their systems and data from cyber threats. Here are some reasons why threat modeling is essential in cybersecurity:
- Identifying Security Risks: Threat modeling helps organizations identify and understand the potential security risks and vulnerabilities in their systems and applications. It enables them to evaluate the possible attack vectors and scenarios hackers may use to exploit their systems.
- Prioritizing Security Controls: Once the security risks have been identified, threat modeling helps organizations prioritize the security controls that need to be implemented to mitigate those risks. Organizations can determine the most effective security measures to implement by understanding the impact and likelihood of potential attacks.
- Early Detection of Vulnerabilities: Threat modeling allows organizations to detect and address potential security vulnerabilities early in development. This reduces the need for costly post-deployment remediation efforts and helps ensure secure systems.
Conclusion
In conclusion, threat modeling is a critical process in cybersecurity that helps organizations identify and mitigate potential security risks and vulnerabilities in their systems and applications. By understanding the attack vectors and scenarios that hackers may use to exploit their strategies, organizations can prioritize the security controls needed to protect their assets. Early detection of vulnerabilities during development can reduce the need for costly post-deployment remediation efforts and ensure that systems are secure from the outset. For more knowledge read our blogs on our website Auxin.io.






