According to Gartner, the Cloud has become the focal point of new digital experiences due to the ongoing pandemic and the rise in digital services. Global cloud revenue is expected to reach $474 billion in 2022, up from $408 billion in 2021. As more businesses use cloud services, managing user identities and access rights has become increasingly challenging. This has resulted in issues such as manual user provisioning, inconsistent access controls, and delayed onboarding and offboarding procedures. These problems not only increase operational costs for IT teams but also pose security risks.
Milind Govekar, an acknowledged thought leader in cloud strategy and distinguished vice president at Gartner, highlights this change by saying, “There is no business strategy without a cloud strategy.” This finding demonstrates how cloud adoption has emerged as a key factor in encouraging new digital experiences across a range of industries, from banks enhancing customer interactions through startups to energy and automotive firms investing in mobile payments.
Organizations are utilizing automated provisioning standards, such as SCIM 2.0, to address these issues because they enable seamless synchronization of users and groups between cloud platforms and identity providers. Centralizing user and group management is made incredibly effective by integrating cloud-based analytics platforms with Azure Active Directory (Azure AD) via SCIM 2.0. Without the need for common manual updates, this integration guarantees that user access is always current and compliant with corporate policies.
Additionally, it simplifies role assignments and lowers errors by supporting complex group memberships while improving security through the use of contemporary authentication techniques. Organizations benefit from a stronger security posture, faster user lifecycle management, and reduced administrative workload when managing their cloud-based analytics platforms in the Cloud environment.
Simplifying User and Group Setup with SCIM 2.0
The automation of user and group provisioning is one of the primary benefits that SCIM 2.0 offers to Cloud-based analytics platforms and Cloud users who utilize Azure AD. In the past, synchronizing users between Cloud-based analytics platforms and an identity provider was a laborious, manual process that was prone to mistakes and delayed updates. Before SCIM, user access was manually managed by IT teams. For users who had left or switched roles, administrators had to update permissions in each application individually. Administrators can set up Azure AD to automatically provision users and groups using SCIM 2.0, ensuring that Cloud-based analytics platforms reflect the current state of the directory.
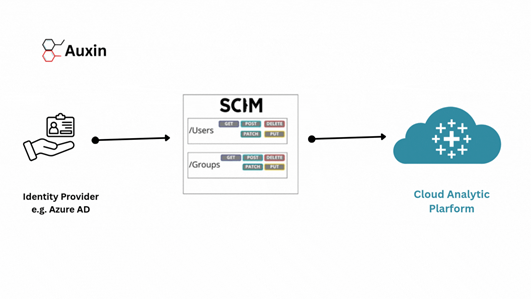
This maintains user data as up-to-date and accurate as possible while eliminating the need for frequent manual intervention, freeing up IT teams to focus on higher-value tasks. Key user attributes, such as site roles, group memberships, and authentication methods, are provisioned by the automation, streamlining and expediting the onboarding and offboarding procedures. The cloud cybersecurity expertise of Auxin Security ensures that strong, customized security measures are in place to protect identity data in cloud environments during this automated provisioning process.
Modern Login Techniques to Increase Security
In the past, basic authentication was frequently used for SCIM provisioning requests between Cloud-based analytics platforms and Azure AD, exposing systems to risks related to the transmission of usernames and passwords. OAuth 2.0 bearer tokens are used for authentication when SCIM 2.0 support is introduced. These tokens provide a secure, cryptographic-protected method for confirming provisioning requests. Bearer tokens significantly lower the risk of unauthorized access through credential compromise because they are application-specific and cannot be used across resources.
In addition to aligning Cloud-based analytics platforms with Azure AD integration and current security standards, this change helps enterprises meet the governance and compliance requirements associated with identity management. Auxin Security helps enterprises implement these contemporary authentication standards while proactively protecting against evolving cybersecurity threats, leveraging its extensive expertise in threat modeling and secure cloud architectures.
Handling Complex Groups with Flexibility
It has historically been challenging to manage identities for users who belong to multiple groups with varying role assignments, especially on platforms that enforce role-based access controls, such as Cloud-based analytics platforms. Users assigned to various groups could result in provisioning conflicts before SCIM 2.0 integration, requiring time-consuming manual checks to ensure users belonged to only one group.
Currently, almost one-third of cyberattacks exploit these unmanaged or shadow IT resources, making manual user management exceptionally challenging. By allowing Cloud-based analytics platforms to automatically assign users the highest permission level among their group memberships, SCIM 2.0 streamlines this process. In large organizations, where users often belong to multiple groups with complex access requirements, this capability is invaluable because it reduces administrative burdens and eliminates errors during provisioning. By offering cloud and container security solutions that protect sensitive access controls and maintain compliance across dynamic group memberships, Auxin Security supports these complex environments.
Taking Control Further with Custom Provisioning Apps
Some organizations require more granular control than standard integrations can provide, despite SCIM 2.0 offering simplified automatic provisioning. This is made possible by Cloud-based analytics platforms and their REST API, which enables the creation of custom provisioning applications. As an illustration, consider the open-source program TabProvision, which allows businesses to personalize the importation and synchronization of user and group data from IdPs such as Azure AD with Cloud-based analytics platforms.
This adaptability can extend provisioning capabilities to on-premises and Cloud-Based analytics platforms, server environments, integrate multiple identity sources, and support intricate workflows. For businesses with specialized or sophisticated provisioning requirements, it offers strong customization, although implementation requires more technical work. To ensure that customization does not compromise security, Auxin Security’s skilled engineering teams collaborate with businesses to develop and deploy such customized DevSecOps and cloud solutions.
Keeping Provisioning Simple and Secure
Organizations will need to implement automated identity and access management systems, such as SCIM 2.0, by 2025 to continue operating securely and effectively in the cloud. The seamless management of users and groups across platforms is becoming a need rather than an option as cloud services continue to advance digital innovation. Auxin Security provides strong protection and compliance in a constantly changing cloud environment by offering organizations professional security solutions and strategic guidance to manage these complexities.






