Secure Software Development: Building a Strong Foundation for Digital Solutions
In today’s interconnected world, software has become integral to our daily lives. The demand for efficient and innovative software solutions is skyrocketing from mobile applications to web platforms. However, this rapid growth also brings along significant security concerns. Cyberattacks, data breaches, and privacy violations have become all too common, leaving individuals and organizations vulnerable. That’s where secure software development steps in. According to Gartner External security testers play an important role in the enterprise secure software development life cycle; however, they are often expensive. This blog post will explore the importance of secure software development and discuss essential practices to build a strong foundation for digital solutions.
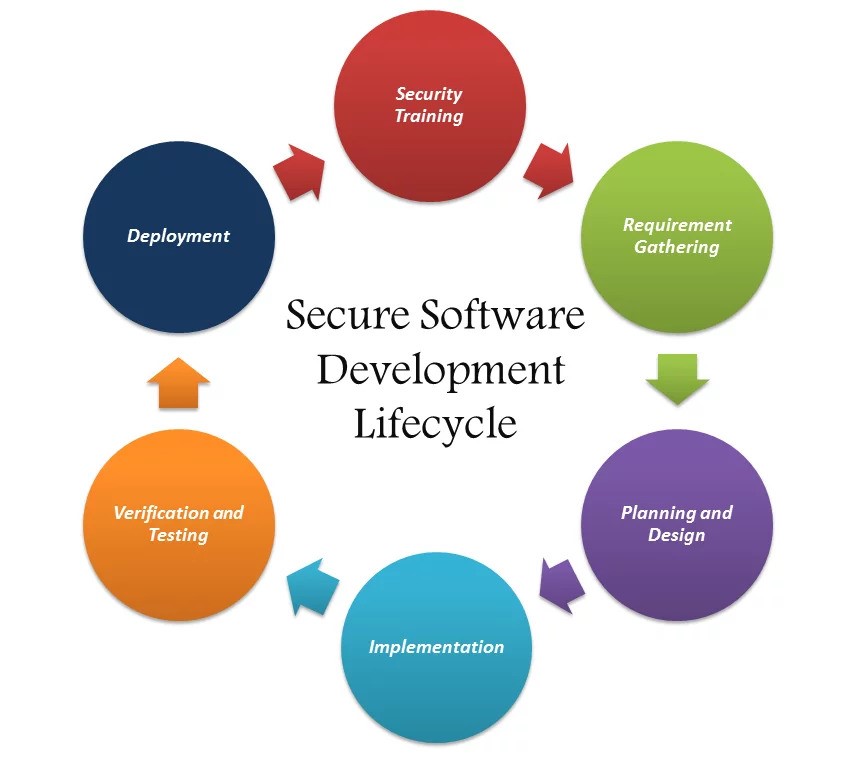
- Understanding Secure Software Development: Secure software development refers to a set of practices and techniques to create resilient software applications against various security threats. It integrates security measures throughout the development lifecycle, from planning and strategy to implementation and maintenance. By prioritizing security from the outset, developers can minimize vulnerabilities and potential risks, ensuring their software remains robust and protected.
- Threat Modeling: An essential step in secure software development is threat modeling. This process involves identifying potential threats and vulnerabilities that could compromise the security of the software. By analyzing the system architecture, data flow, and potential attack vectors, developers can comprehensively understand the security risks. This enables them to design and implement appropriate security controls and countermeasures proactively.
- Secure Coding Practices: Secure coding practices play a crucial role in reducing common vulnerabilities in software. Developers should follow industry best practices and adhere to safe coding guidelines. This includes:
Security Training and Awareness:
Developers and other stakeholders involved in software development should receive proper security training and be aware of common security threats and best practices. Building a security-conscious culture within the development team helps foster a proactive approach to software security. Encouraging ongoing education, staying updated on the latest security trends, and promoting communication channels for reporting and addressing security concerns are essential aspects of this practice.
Patching and Updates:
Software vulnerabilities are continually discovered, and it’s crucial to address them through regular patching and updates promptly. Developers should have a well-defined process for monitoring security advisories, applying patches, and releasing updates to address identified vulnerabilities. This proactive approach helps protect users and mitigate the risk of exploitation.
Secure Deployment and Infrastructure:
Secure software development extends beyond the code itself. It also encompasses fast deployment and infrastructure practices. This includes securely configuring servers, managing access controls, implementing firewalls and intrusion detection systems, and applying security updates to the underlying infrastructure. By considering the entire software ecosystem, developers can reduce the overall attack surface and enhance the security posture.
Conclusion:
Secure software development is no longer an option; it is necessary in today’s digital landscape. Organizations can build robust software solutions that protect user data, preserve privacy, and withstand ever-evolving threats by prioritizing security throughout the development process. Incorporating threat modeling, secure coding practices, training, patching, and secure deployment strategies are essential steps toward creating a secure software development lifecycle. For more knowledge read our blogs on our website Auxin.io.






