Mitigating DoS and DDoS Attacks with Auxin Security’s Expertise
According to recent Gartner’s insights, denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks have remained persistent and highly disruptive threats in the digital landscape. These attacks, which overwhelm systems by flooding them with excessive traffic or exploiting vulnerabilities to crash networks, have seen a significant increase, with DDoS attacks growing by 150% globally in 2022. High-profile organizations, particularly in banking, e-commerce, media, and government sectors, are prime targets for such assaults. The consequences are severe—downtime, reputational harm, financial losses, and customer attrition—making these attacks a serious challenge for businesses and public institutions alike.
The distributed nature of DDoS attacks, where traffic is launched simultaneously from thousands of infected “bot” computers globally, makes them particularly difficult to defend against. Attackers can mask their locations, making detection and mitigation even more challenging. As hackers continue to use these tactics to sabotage web properties and inflict widespread disruption, organizations must bolster their cybersecurity frameworks. This includes deploying robust DDoS protection, real-time monitoring, and proactive response strategies to minimize damage and maintain service continuity. In an era where cyber threats are increasingly sophisticated, vigilance and advanced security measures are critical to defending against the growing wave of DoS and DDoS attacks.
How does a DoS attack work?
A Denial-of-Service (DoS) attack works by overwhelming a target machine, server, or network with an excessive amount of traffic or sending malicious requests that cause the system to crash or slow down. The goal of a DoS attack is to make the target inaccessible to its legitimate users, disrupting normal operations. DoS attacks can be executed in two main ways:
1. Flood Attacks:
In a flood-based DoS attack, the attacker bombards the target system with more traffic than it can handle. This excessive traffic consumes the target’s bandwidth, memory, or processing power, causing the system to slow down or shut down entirely. Various types of flood attacks include:
- ICMP Flood (Ping Flood): The attacker sends an overwhelming number of ICMP (Internet Control Message Protocol) echo requests (pings) to the target, overloading its network resources.
- SYN Flood: The attacker sends a barrage of SYN (synchronization) requests to the target server, initiating numerous half-open connections that exhaust the server’s resources and prevent legitimate connections.
- UDP Flood: Large amounts of User Datagram Protocol (UDP) packets are sent to random ports on the target, causing it to use up resources trying to process these requests.
2. Crash Attacks:
In a crash-based DoS attack, the attacker exploits a vulnerability in the target system by sending malformed or malicious data that causes the system to malfunction. This can lead to a slowdown or complete crash, making the target unavailable to users. For example, a buffer overflow attack sends more data than a system’s buffer can handle, leading to a system crash.
In both types of DoS attacks, the result is that legitimate users are unable to access the targeted service, causing disruptions in business operations, financial losses, and potential reputational damage for the victim organization.
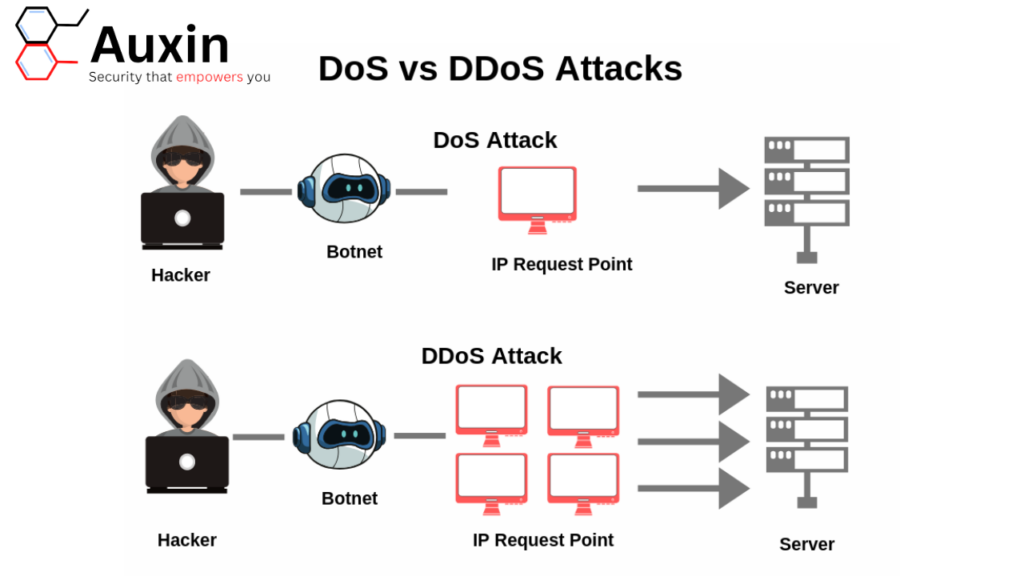
What is the difference between a DDoS attack and a DOS attack?
The key difference between a DoS (Denial-of-Service) attack and a DDoS (Distributed Denial-of-Service) attack is the number of sources involved. In a DoS attack, a single source or attacker overwhelms a target system or network with excessive traffic or malicious requests, making it unavailable to legitimate users. In contrast, a DDoS attack is distributed, meaning the attack originates from multiple sources or systems (often compromised devices known as botnets), which simultaneously flood the target with traffic, making it harder to mitigate since the traffic comes from various locations around the world.
How Auxin Security Can Help
Gartner’s insights on the rise of DoS and DDoS attacks highlight the growing need for robust, multi-layered cybersecurity solutions. Auxin Security, with its expertise across various domains like Cybersecurity, Data Protection, and Governance, Risk & Compliance (GRC), is uniquely positioned to help organizations defend against these escalating threats.
Through cybersecurity services, Auxin can implement advanced network monitoring and threat detection mechanisms to identify and mitigate DoS/DDoS attacks in real-time. By leveraging Data Protection expertise, Auxin ensures that critical data remains secure even during large-scale attacks, minimizing potential breaches or data corruption. In the realm of Governance, Risk & Compliance, Auxin provides comprehensive frameworks to ensure businesses are not only compliant with regulations but are also resilient against evolving cyber threats. Through Audit & Assessment, Auxin helps organizations identify vulnerabilities, enabling them to proactively shore up defenses before they can be exploited by attackers.






