According to Forbes, cybercrimes are expected to reach $10.5 trillion annually by 2025, and organizations urgently need to implement adequate security measures. A maximum of 95% of companies had at least one data breach, becoming a more significant environment. More businesses increasingly rely on digital infrastructure, which has the risk of exploitation, so companies must adopt proactive strategies that address weaknesses before they can be exploited. Auxin Security empowers organizations to address these problems efficiently and offers a balanced security and risk management solution.
Threat modeling emerges as a critical solution for identifying enabling organizations and evaluating potential threats to their systems. A Tufts Security and Privacy Lab study shows that companies using threat modeling techniques reduce risk exposure by up to 50%. Businesses can enhance their understanding of vulnerabilities and implement targeted countermeasures using structured methodologies such as STRIDE, DREAD, and PASTA.
Understanding of Threat Modeling
Threat modeling is a proactive strategy for identifying and communicating information about threats to a system or network. It enables IT departments to understand these risks’ potential impacts and nature, allowing for a more strategic defense against cyber attacks. Organizations can develop a robust security posture by analyzing current threats and anticipating future risks.
For instance, bank information security studies showed that 60% of companies suffered a data breach caused by unpatched vulnerabilities. This highlights the importance of proactive threat modeling in identifying and addressing these threats before they become exploited.
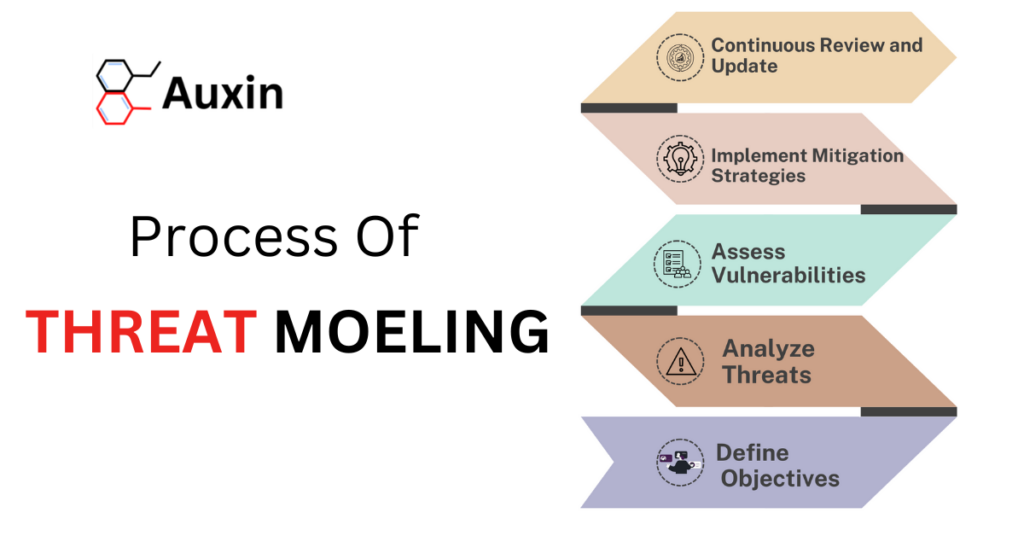
Threat Modeling Process
Threat modeling is a systematic approach that allows businesses to identify, analyze, and reduce potential threats to systems. The processes aim to understand the threat environment thoroughly and constitute a systematic approach. Below is a detailed analysis of relevant data and research in the field.
- Define Objectives: Establish clear goals for threat modeling practice. According to the 2024 Forbes study, 65% of companies list a lack of skilled personnel as a significant barrier to good security policies. Defining goals helps align the threat modeling process with resource allocation and organizational goals. Auxin Security’s expertise clarifies goals that align with its specific operational requirements and challenges.
- Analyze Threats: Systematically identify potential threats and utilize frameworks like STRIDE or DREAD. For example, the Tahawultech Report for 2024 highlights that cybercriminals exploit new vulnerabilities 43% quicker than in any other previous year. This urgent need for attention through analysis is to stay for proactive defense. Auxin Security helps organizations offer expert consultation to thoroughly analyze threats, ensuring a comprehensive understanding of the threat landscape.
- Assess Vulnerabilities: Examine existing security systems and identify gaps. According to a Ponemon Institute study, organizations with vulnerability management plans can reduce their breach costs by about $1.2 million per incident. This evaluation can help determine where changes are required. Auxin Security offers custom vulnerability assessments highlighting significant flaws, enabling organizations to prioritize and address them effectively.
- Implement Mitigation Strategies: Develop targeted countermeasures based on identified risks. According to a Cybersecurity Insiders study, 71% of organizations intend to increase their expenditure on threat detection and response tools in 2025. This step involves prioritizing actions that effectively reduce risk exposure. Auxin Security helps develop robust mitigation strategies that integrate industry best practices, ensuring efficient organizational risk management.
- Continuous Review and Update: Regularly assess the performance of executed strategies against evolving threats. The cyber security environment is dynamic, and ongoing monitoring is essential. The Verizon Data Breach Investigations Report (DBIR) emphasizes the need for constant awareness and adjustment, stating that 80% of breaches result from human mistakes or system misconfigurations. Auxin Security emphasizes ongoing monitoring and adaptation of security measures, helping organizations stay ahead of emerging threats in a dynamic environment.
Threat Modeling Frameworks
Threat modeling frameworks provide a structured approach to locating and mitigating potential systems and application threats. STRIDE allows teams to evaluate vulnerabilities systematically and categorizes threats into six categories: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service (DoS), and Elevation of Privilege. DREAD assesses threats based on damage potential, reproducibility, exploitability, affected users, and discoverability.
While PASTA incorporates threat modeling into DevOps workflow for streamlined processes, the model includes seven steps that help businesses define goals and evaluate threats. Each methodology allows the company to assess risks and implement adequate security measures customized to its environment. Auxin Security’s expertise in these frameworks ensures tailored solutions that improve an organization’s security posture.
Final Words
Effective threat modeling is significant for organizations to identify and address vulnerabilities within their systems and applications proactively. Businesses can enhance their understanding of potential threats and implement targeted countermeasures like STRIDE, DREAD, and PASTA. This comprehensive approach strengthens security measures and fosters resilience against the evolving landscape of cyber threats.