Cloud Access Security Broker (CASB)
Today’s company operations are primarily dependent on cloud computing. Cloud enables businesses to access programs and store data remotely, lowering infrastructure costs and enhancing flexibility. As demonstrated by Auxin’s research, there are also new security issues due to the growth of cloud computing. The requirement to safeguard data and applications no longer hosted on-premises is one of these biggest obstacles. A Cloud Access Security Broker (CASB) can help in this situation. This blog will introduce you to what a CASB is and how it operates inline in the cloud operation. Auxin Security is a cyber security leader, and our team of experts has led the digital transformation across multiple Fortune 100 firms across the globe.
What is Cloud Access Security Broker?
A Cloud Access Security Broker (CASB) is a security tool between a company’s internal infrastructure and the cloud service provider’s infrastructure. It serves as a gatekeeper, monitoring all communication between them and enforcing security regulations. A CASB gives businesses access, control, visibility, and protection against cloud apps and data threats. In this blog, we’ll examine the advantages of CASB usage and how it can assist businesses in securing their cloud environments.
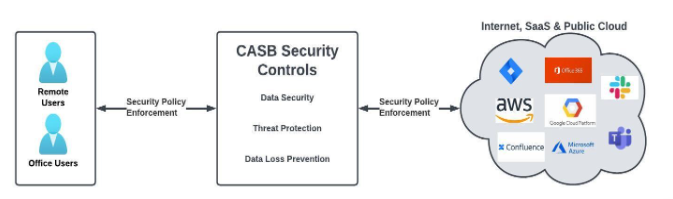
What advantages does a Cloud Access Security Broker offer?
- Visibility and Control
One significant advantage of adopting a CASB is having more visibility and control over cloud data and apps. A centralized view of all cloud applications and data used by a company is provided by CASBs. With this awareness, IT professionals can find shadow IT apps that are being utilized without authorization and take action to regulate them. Additionally, it enables IT departments to monitor user behavior and ensure that users are only using the programs and data they require.
CASBs offer fine-grained management over cloud apps and data in addition to visibility. Businesses can use CASBs to set access rules for cloud applications and data. These regulations may depend on several variables, including the user, device, location, and activity. For instance, a business may establish a policy that restricts access to a cloud service to users from geographies or that only permits certain users to use a particular cloud application. The ability to implement security regulations like data loss prevention (DLP) and encryption is another feature offered by CASBs.
- Threat Protection
Threat protection is a crucial advantage of CASB use. Malware, phishing, and data breaches are just a few of the hazards to which cloud systems are vulnerable. A CASB offers several security elements that aid in defending against these dangers. A CASB, for instance, can prohibit any dangerous behavior by scanning all incoming and outgoing data for malware. It may also recognize phishing attempts and prevent users from accessing phishing websites.
Moreover, CASBs include threat intelligence tools that let businesses proactively identify and reduce risks. Among the threat intelligence features are machine learning algorithms that recognize odd behavior, such as a person accessing data from an unusual location or time. Moreover, CASBs can send IT teams instant notifications concerning questionable activities.
- Compliance and Governance
The core components of any organization’s security plan are compliance and governance. Businesses that use cloud apps and data are required to abide by several laws, including GDPR, HIPAA, and PCI DSS. CASBs can assist businesses in complying with these regulations by offering a variety of functions like data discovery, data classification, and compliance reporting.
Businesses can locate sensitive data stored in cloud applications and data thanks to data discovery features. The ability to categorize data according to its sensitivity and then apply the necessary security measures is provided by data classification features. Compliance reporting features provide reports that show compliance with regulations.
Conclusion
Companies that use cloud apps and data can profit from cloud access security brokers (CASBs) in a few ways. Threat protection, visibility, control over cloud apps and data, and assistance in meeting compliance and governance needs, are all provided by CASBs.
The demand for CASBs will rise along with the growth of cloud computing. Businesses employing cloud applications and data ought to consider including a CASB in their overall security plan. Auxin security can assist from a high-level introduction to CASB to details implementation, including solution architecting within your cloud and application ecosystems.






