Introduction: In today’s interconnected world, where cyber threats loom large, organizations must fortify their digital assets against potential breaches. Penetration testing, also known as ethical hacking, is a crucial practice that helps identify vulnerabilities and strengthen the security posture of systems and applications. This blog post explores the world of penetration testing, its objectives, methodologies, and the role it plays in enhancing overall cybersecurity.
Large organizations spend thousands of dollars on software product manufacturing but often compromise on the security domain. Cyber attacks have evolved with technology upgrades; when organizations face a cyber attack, the dimension is reversed, and the same companies spend vast sums of money to safeguard their products. To refrain oneself from assaults like this, security should be a top priority from the start. No product is hundred percent secure, but taking necessary precautions limits the percentage of facing an attack. One very famous security testing method is penetration testing (pen testing).
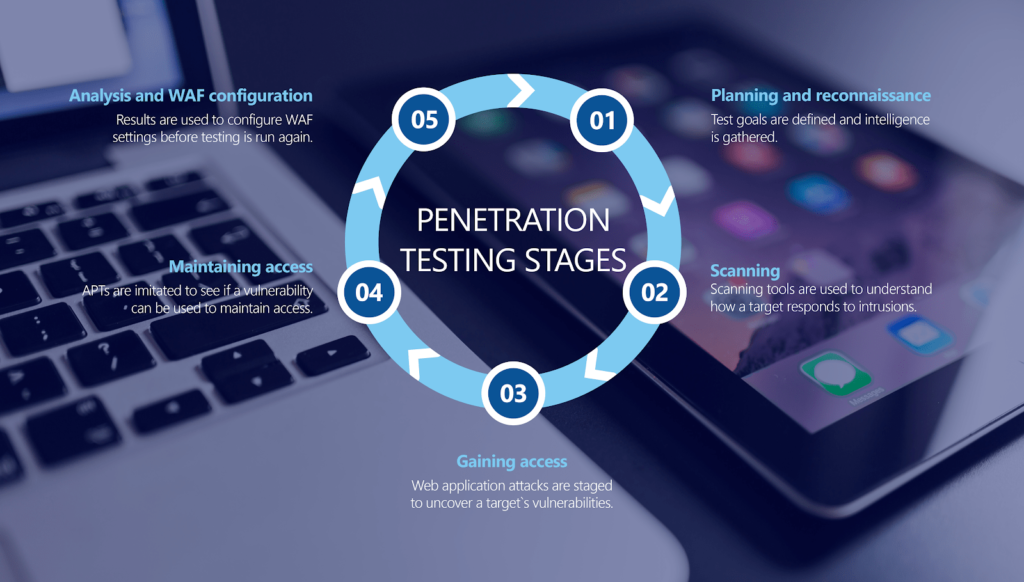
In penetration testing, an official team of IT professionals tries to attack your system in every possible way. The group includes your internal security team and hired ethical hackers to test every vulnerability. The main priority is to check whether the system is robust enough to bear attacks initiated by authenticated or unauthenticated users. Performed correctly, a pen test can dive into the system and test it from every aspect.
Comprehensive pen testing can be ruled for many types, such as
- Web Applications
- Mobile Applications
- Network
- Cloud
- IOT
- APIs
- Pipelines Framework
Pen testing is better than automated security testing as it dives deep into the business logic; this enables us to find more flaws that are not done in automated testing. Automated testing follows a list of vulnerabilities listened to in OWASP. Still, a pen test is better because it doesn’t follow a predetermined list.
With security breaches becoming increasingly severe each year, large organizations now need a more visible security plan that determines how they will fight if they ever get attacked. Pen testing allows you to understand the flaws in your code, architecture style, and other cyber assault-assessing techniques.
Another way penetration tests can assist your business lies in regulation and compliance with current standards. A pen test ensures that your system’s design meets current constraints or updates. These early detections help you to fix these problems to ensure that your business is fully compliant where it needs to be.
Conclusion: Penetration testing is an essential practice in today’s cybersecurity landscape, helping organizations identify and address vulnerabilities before malicious actors can exploit them. By understanding the purpose, methodologies, and best practices of penetration testing, organizations can significantly enhance their security posture and safeguard their valuable digital assets from emerging threats.
A pen test will report all the areas where work needs to be done. This allows you to allocate money in vulnerable areas, not investing considerable sums to make it all again. Hence, pen test is now a necessary evil. It needs to be addressed where critical data organizations are at risk. For more insightful blogs visit auxin.io






