Auxin’s Risk Based Approach to Penetration Testing and Vulnerability Assessments
Penetration testing, often referred to as pen testing, is a proactive approach to assessing the security of a computer system, network, or application by simulating real-world cyber-attacks. The primary goal of penetration testing is to identify vulnerabilities that could be exploited by malicious actors. This process involves a thorough analysis of the target system’s infrastructure, followed by attempts to exploit weaknesses using various tools and techniques. Penetration testing helps organizations understand their security posture and provides actionable insights to mitigate potential risks, ultimately enhancing overall cybersecurity resilience.
In essence, penetration testing is akin to having a skilled ethical hacker attempt to break into your systems, but with the intent of improving security rather than causing harm. It involves comprehensive testing methodologies, including reconnaissance, scanning, exploitation, and post-exploitation analysis. By conducting penetration tests regularly, organizations can proactively identify and address security flaws before they are exploited by malicious attackers, thus bolstering their defenses and safeguarding sensitive data and resources.

Penetration Testing vs. Vulnerability Assessments
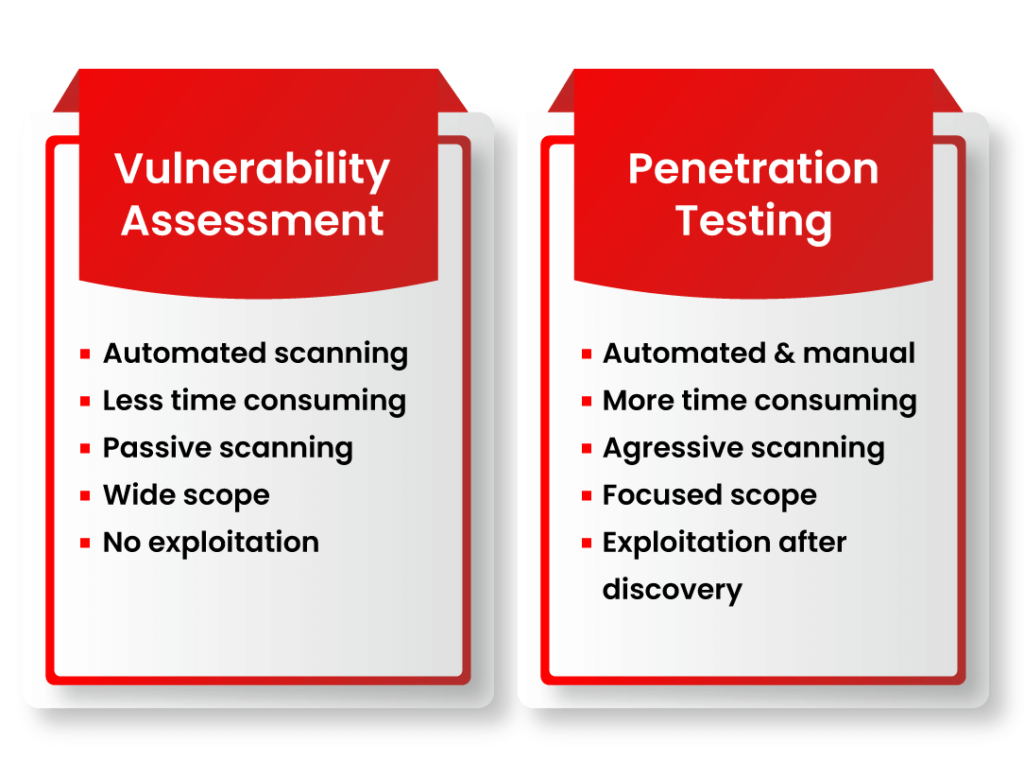
Penetration testing and vulnerability assessments are both crucial components of a robust cybersecurity strategy, but they serve different purposes and have distinct methodologies. Penetration testing involves simulating real-world attacks to identify and exploit vulnerabilities in a system, network, or application. It goes beyond vulnerability assessments by actively attempting to breach defenses, providing a more in-depth understanding of potential security risks and their potential impact. Penetration testing often involves manual testing by skilled professionals, as well as automated tools, to uncover vulnerabilities that might not be detected through automated scans alone.
However, vulnerability assessments focus on identifying and categorizing vulnerabilities within an organization’s systems, networks, or applications. These assessments typically involve automated scans that detect known vulnerabilities and weaknesses, providing a comprehensive inventory of potential security issues.
Penetration Testing vs. Vulnerability Scanning
Penetration testing and vulnerability scanning are both integral parts of a comprehensive cybersecurity strategy, but they serve distinct purposes and employ different methodologies. Penetration testing involves simulating real-world cyber-attacks to identify and exploit vulnerabilities in systems, networks, or applications. It goes beyond vulnerability scanning by actively attempting to breach defenses, providing a deeper understanding of potential security risks and their impact. Penetration testing often involves manual testing by skilled professionals, alongside automated tools, to uncover vulnerabilities that might evade automated scans.
Conversely, vulnerability scanning focuses primarily on identifying known vulnerabilities within an organization’s systems, networks, or applications. It involves automated scans that detect and categorize vulnerabilities based on predefined criteria. Vulnerability scanning provides a snapshot of existing weaknesses, enabling organizations to prioritize and address them based on severity and potential impact.
However, unlike penetration testing, vulnerability scanning does not involve actively exploiting vulnerabilities to assess their real-world implications. Instead, it offers a systematic approach to identifying potential security issues, helping organizations maintain an up-to-date inventory of vulnerabilities and ensure timely remediation efforts. In summary, while penetration testing involves actively probing for vulnerabilities through simulated attacks, vulnerability scanning focuses on automated detection and categorization of known weaknesses.
What are the types of pen testing
There are several types of pen testing, each focusing on different aspects of security:
- Black Box Testing: Also known as external testing, the tester has no prior knowledge of the system being tested. This simulates an attack by an external hacker who has limited information about the target system.
- White Box Testing: Also called internal testing, the tester has full knowledge of the system being tested, including source code, network diagrams, and system architecture. This allows for a more thorough assessment of security controls.
- Gray Box Testing: A combination of black box and white box testing, where the tester has partial knowledge of the system. This approach simulates an attack by a malicious insider or someone with limited access to the system.
- Web Application Testing: Specifically targets web applications to identify vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms.
- Mobile Application Testing: Focuses on assessing the security of mobile applications running on various platforms such as iOS and Android. This includes testing for vulnerabilities related to data storage, communication, and authentication.
Auxin’s Penetration Testing: Enhancing Cybersecurity Resilience
Auxin’s Penetration Testing services offer a proactive approach to cybersecurity, serving as a shield for your digital assets in today’s complex threat landscape. Penetration testing involves simulating cyberattacks to identify vulnerabilities in your systems, networks, and applications before malicious actors exploit them. By partnering with Auxin, you gain access to comprehensive insights into your security posture, enabling you to address weaknesses and bolster your defenses effectively.
With Auxin’s expert penetration testing, you’re not just reacting to potential threats; you’re actively staying ahead of them. By uncovering vulnerabilities proactively, you can mitigate risks and prevent potential breaches before they occur. This proactive stance is crucial in safeguarding your organization’s sensitive data, reputation, and financial assets.
Auxin’s penetration testing expertise empowers your organization to:
- Identify Weaknesses: Through meticulous testing methodologies, Auxin pinpoints vulnerabilities across your digital infrastructure, including networks, applications, and systems.
- Prioritize Remediation: By understanding the severity of vulnerabilities, you can prioritize remediation efforts, allocating resources efficiently to address critical risks first.
- Enhance Security Posture: Armed with actionable insights, you can implement robust security measures to fortify your defenses, thereby reducing the likelihood of successful cyberattacks.
- Stay Ahead of Threats: In the ever-evolving landscape of cybersecurity threats, staying ahead is paramount. Auxin’s penetration testing keeps you abreast of emerging risks, enabling proactive measures to thwart potential attacks.
- Ensure Regulatory Compliance: Compliance with industry standards and regulations is essential for many organizations. Auxin’s penetration testing helps ensure your adherence to relevant compliance requirements by identifying and addressing security gaps.
By elevating your security posture with Auxin’s trusted penetration testing services, you demonstrate a commitment to safeguarding your organization’s assets and maintaining trust among stakeholders. With Auxin as your partner, you can navigate the complexities of cybersecurity with confidence, knowing that your defenses are fortified against evolving threats.






