Unleashing the Power of Policy as Code: New Age of Automation and Agility
In today’s rapidly evolving digital landscape, the need for robust security practices has never been more critical. As organizations grapple with the complexities of securing their digital assets, a revolutionary approach is emerging: Policy as Code. This transformative concept blends software development principles with security policies, offering a dynamic and automated way to enhance security postures.
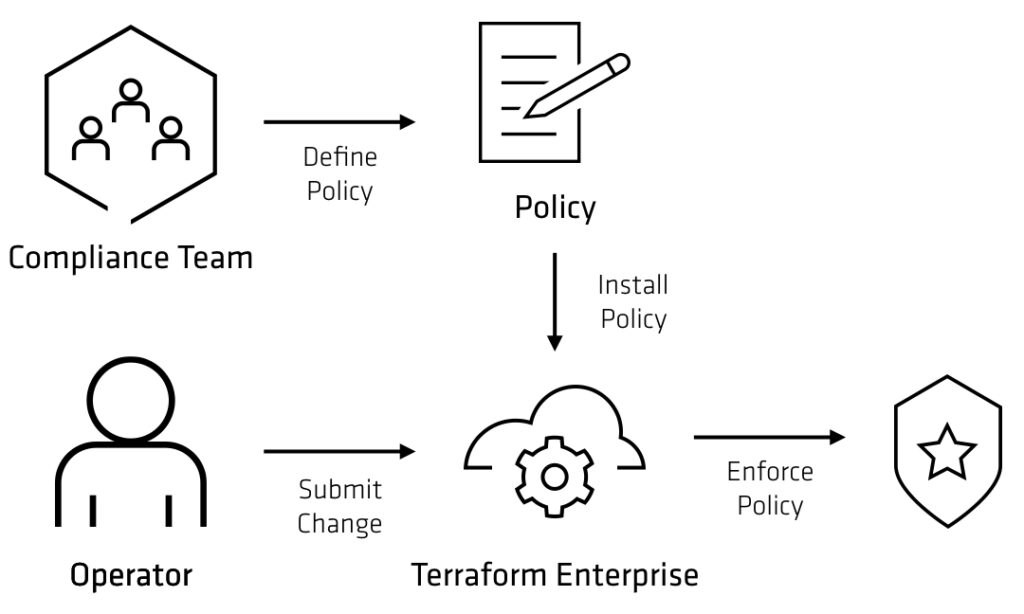
The need for developing Policy as Code arose from the ever-growing complexity of modern IT environments and the imperative for robust cybersecurity practices. Traditional methods of managing security policies were often manual, error-prone, and lacked the agility to keep pace with dynamic digital ecosystems. Policy as Code addresses these challenges by codifying security policies into machine-readable scripts or codes.
How it works
At its core, Policy as Code is codifying security policies into machine-readable Code. This Code can then be deployed and enforced programmatically, automating security checks and ensuring compliance in a way that was previously cumbersome and error-prone. This concept is closely related to Infrastructure as Code (IaC), where infrastructure configurations are defined in Code, and changes are automated.
This approach is a game-changer for security. Traditionally, security policies were documented in lengthy, static documents, often leading to human error when translating into actionable controls. With Policy as Code, policies become executable, reducing the likelihood of human errors and enabling rapid and consistent policy enforcement.
Enhanced Security through Automation
Policy as Code automates security checks, offering real-time enforcement of policies. This automation not only accelerates the identification and mitigation of security vulnerabilities but also improves the scalability of security practices. It ensures that security policies are consistently applied across diverse environments, reducing the attack surface and enhancing overall cybersecurity.
Organizations can perform continuous compliance monitoring by codifying security policies instantly and identifying deviations from security standards. This real-time visibility into the security posture allows for immediate remediation, bolstering an organization’s ability to respond to emerging threats swiftly.
Challenges and Future Possibilities
While Policy as Code holds immense promise, it has challenges. Developing, maintaining, and testing policy code can be complex, and organizations must invest in the tools and skill sets to fully embrace this paradigm shift. Furthermore, there’s a need for standardized policy languages and frameworks to ensure interoperability and ease of adoption.
Looking ahead, the future of Policy as Code is bright. We can expect further innovation, including developing more sophisticated policy engines and integrating emerging technologies like artificial intelligence and machine learning. These advancements will enable organizations to automate policy enforcement and make predictive security decisions based on real-time data analysis.
Embracing the Transformation
As a technologist, I view Policy as a Code of excitement and anticipation. This paradigm shift aligns with the principles of DevSecOps, where security is integrated into the development and deployment pipeline. It empowers DevOps Engineers to proactively identify and address security issues early in the SDLC, reducing the cost and impact of security incidents.
By adopting Policy as Code, cybersecurity firms can streamline and automate enforcing security policies for their clients. This improves the efficiency of security operations and ensures that policies are consistently and accurately applied across complex IT environments. Additionally, the real-time enforcement capabilities of Policy as Code allow cybersecurity companies to rapidly identify and respond to security threats, reducing the potential impact of breaches.
In conclusion, Policy as Code represents a transformative approach to cybersecurity that offers efficiency, consistency, and agility. We are responsible for embracing this paradigm shift, acquiring the required expertise, and collaborating across teams to ensure our organizations are secure in the ever-evolving digital frontier. The future of cybersecurity is in Code, and it’s an exciting journey we’re embarking on. For more interesting blogs, visit auxin.io






