According to a recent Gartner’s report, SQL injection is a type of attack where malicious SQL statements are injected into an application’s input fields, exploiting vulnerabilities in the code to gain unauthorized access to databases. These databases, which form the backbone of most data-driven websites and applications, use Structured Query Language (SQL) to manage data, making them common targets. By entering a crafted SQL query, attackers can manipulate the database, bypass security controls, and access sensitive information. As an example, a 2020 breach at Freepik Company impacted over eight million users’ login data due to an SQL injection vulnerability, underscoring how prevalent and damaging these attacks can be.
Because so many web applications rely on relational databases, SQL injection attacks remain widespread and potentially devastating. A successful SQL injection can allow attackers to view, modify, or delete data, execute administrative tasks, or, in some cases, even issue operating system commands. The Common Vulnerabilities and Exposures (CVE) database lists over 15,000 entries related to “injection” attacks, emphasizing how frequently these vulnerabilities occur. Defending against SQL injection requires rigorous input validation, secure coding practices, and regular security audits to ensure databases are adequately protected.
The Ongoing Threat of SQL Injection
SQL injection (SQLi) remains a critical threat in cybersecurity, with alarming recent statistics highlighting its prevalence. SQLi accounts for nearly 65% of all web application attacks, as reported by Imperva, largely due to common issues like poor input sanitization. The Open Web Application Security Project (OWASP) 2023 report continues to list SQL injection among the top ten web vulnerabilities, underscoring the persistence of this threat. Beyond frequency, the financial repercussions are considerable, with the Ponemon Institute estimating that data breaches involving SQL injection costs can exceed $3.86 million per incident, factoring in data loss, reputational damage, and recovery expenses.
Recent incidents further showcase the risk, such as a 2023 breach affecting 2.3 million users on a gaming platform, where attackers leveraged SQLi to access login credentials and payment details. Another breach in 2022 targeted a healthcare provider, exposing sensitive medical data of over 1.5 million patients. The growing number of recorded vulnerabilities over 15,000 SQLi-related entries in the CVE database underscores the need for robust defenses. For businesses, the stakes are high, as SQLi attacks can lead to costly non-compliance fines under regulations like GDPR and HIPAA, especially when personal or financial data is compromised.
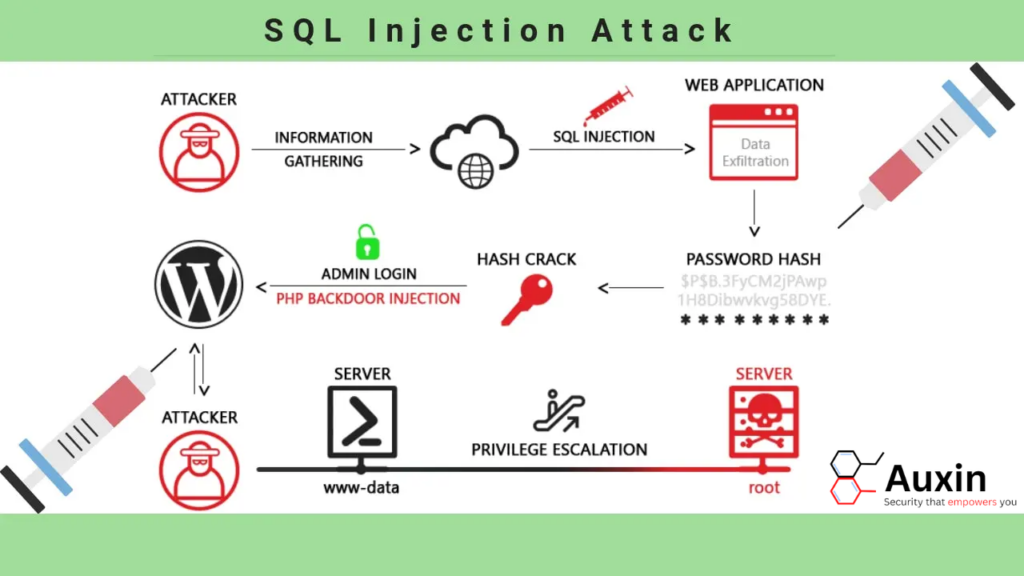
How an SQL Injection Attack is Performed
An SQL injection attack begins when an attacker enters a crafted SQL statement or command into an input field on a website or app—such as a login form, search box, or URL parameter—that interacts with a relational database. The aim is to trick the application into executing unintended commands. Here’s a basic outline of how it works:
- Input Field Exploitation: An attacker targets an input field that accepts user data, like a username and password box. Instead of entering valid information, the attacker types in a specially crafted SQL command.
- Bypassing Authentication: If the application doesn’t properly validate or sanitize inputs, the malicious SQL code is sent to the database as part of the normal query. In some cases, this can allow attackers to bypass authentication by modifying SQL queries to provide unauthorized access, for example by tricking the application into logging in without a password.
- Data Extraction or Manipulation: Once in, attackers can perform additional commands to view, alter, or delete data. For example, a successful SQL injection can provide access to sensitive data like user credentials, payment information, or customer details. The attacker may also gain the ability to modify data or control other elements within the database.
- Advanced SQL Commands: In advanced cases, attackers can leverage “blind” SQL injection to retrieve data even without visible error messages. Using timing delays or conditional responses, attackers gather information over time without triggering alerts. Some sophisticated attacks may even execute operating system commands if the database permissions are lax.
Why SQL Injection Attacks are Performed
The motivation behind SQL injection attacks varies, but the primary reasons include:
- Data Theft: One of the main objectives is to access and steal sensitive data, such as login credentials, financial records, or personally identifiable information (PII). This information can be sold on the dark web, used for identity theft, or leveraged for other attacks.
- Financial Gain: Attackers can exploit SQL injection to steal payment information or customer data, which can then be sold or used for financial fraud. Some attackers may demand a ransom from the compromised company to avoid leaking the data.
- Disrupting Operations: SQL injection can also be used to corrupt or delete critical data, causing operational disruptions for businesses and organizations. This may be part of a larger goal, such as corporate sabotage, or could serve as a method for protest or “hacktivism.”
- Access to Backend Systems: In some cases, SQL injection attacks provide entry points to further exploit a company’s infrastructure. If attackers gain admin-level database access, they may have control over servers, enabling more extensive network intrusions and possibly exposing other critical systems.
- Testing Security Defenses: Some cybercriminals test SQL injection as part of a broader attempt to evaluate the security measures of a target. Successful exploitation often reveals weaknesses that can be leveraged for future attacks or sold to other malicious actors.
The Role of Auxin Security in Defending Against SQL Injection Attacks
Auxin Security is dedicated to helping businesses strengthen their defenses against SQL injection and other cyber threats. With a focus on comprehensive cybersecurity solutions, Auxin Security leverages advanced DevSecOps tooling, secure coding practices, and rigorous security assessments to mitigate vulnerabilities in web applications and databases. Auxin’s solutions are built to empower businesses by embedding security within the development lifecycle, ensuring that applications are protected against SQL injection and other attack vectors from the start.
Through detailed security assessments, vulnerability scanning, and expert guidance, Auxin Security enables organizations to identify and remediate weaknesses in their databases and applications. Our team of seasoned security engineers provides targeted recommendations and actionable strategies, including input validation, parameterized queries, and the implementation of web application firewalls (WAFs) to protect against SQL injection. Auxin Security’s solutions also integrate Governance, Risk, and Compliance (GRC) to meet industry standards, helping companies build resilient defenses and maintain secure environments as they grow.






