Eldorado Ransomware: The New Dual-Threat Targeting Windows and Linux – Insights from Auxin Security
The latest addition to the list of formidable adversaries is ‘Eldorado,’ a complex Ransomware-as-a-Service (RaaS) that targets both Windows and Linux systems. In this blog post, we will delve into what makes Eldorado particularly dangerous, how it operates, and steps you can take to protect your systems from this emerging threat.
What is Ransomware-as-a-Service?
Ransomware-as-a-Service (RaaS) is a business model where cybercriminals develop ransomware and lease it out to other attackers. This allows even those with limited technical skills to launch ransomware attacks. In return, the developers receive a cut of the ransom payments. This model has proliferated in recent years, making sophisticated ransomware more accessible and increasing the frequency and severity of attacks.
The Emergence of Eldorado
Eldorado is a new entrant in the RaaS market, but it has already made a significant impact. First identified in early 2024, Eldorado is designed to target both Windows and Linux systems, making it highly versatile and dangerous. Its dual-platform capability allows attackers to maximize their reach and increase the potential damage to organizations that use mixed operating environments.
How Eldorado Operates
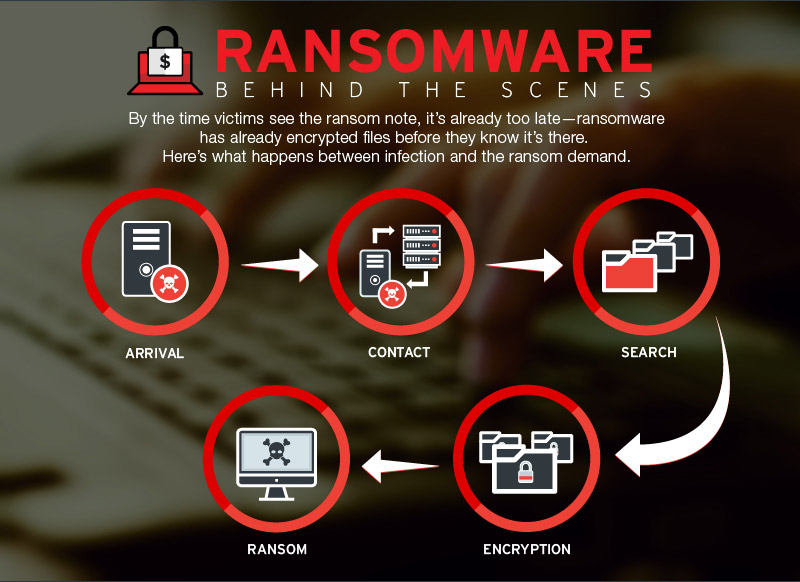
Infection Vectors
Eldorado employs multiple infection vectors, including phishing emails, malicious downloads, and exploiting known vulnerabilities in software and systems. Once inside a network, it uses advanced techniques to escalate privileges and move laterally, making it difficult to contain.
Encryption and Ransom Demands
Once Eldorado has infiltrated a system, it executes a devastating encryption process using robust algorithms, effectively locking down critical files and making them completely inaccessible to users and administrators alike. This encryption process is designed to be virtually unbreakable without the decryption key, which only the attackers possess. As a result, organizations find themselves unable to access vital data necessary for their operations, causing significant disruption and potentially severe financial losses.
In addition to encrypting files, Eldorado leaves behind a ransom note designed to intimidate and coerce victims into complying with its demands. This note typically demands payment in cryptocurrency, commonly Bitcoin or Monero, due to the anonymity and difficulty in tracing transactions associated with these currencies. The ransom note often includes instructions on how to make the payment and may impose a deadline, after which the decryption key might be destroyed or the ransom amount increased.
Stealth and Persistence
Eldorado is meticulously crafted to circumvent detection by conventional antivirus and anti-malware solutions. It employs a suite of sophisticated techniques to achieve this, including obfuscation, where its code is intentionally obscured to evade signature-based detection methods. Furthermore, Eldorado may leverage code signing, using legitimate digital certificates to cloak its malicious activities under the guise of authenticity.
Moreover, Eldorado establishes robust persistence mechanisms within compromised systems. By creating hidden files, altering registry entries, or employing other stealthy tactics, it ensures its continued presence even if initial attempts to remove it are successful. These persistence measures enable Eldorado to maintain control over compromised systems, prolonging its threat and exacerbating the impact on affected organizations.
Protecting Against Eldorado
According to Auxin Security, defending against it requires a multi-layered approach. Here are some essential steps to enhance your cybersecurity posture:
1. Regular Backups
Regularly backing up your critical data is essential for protecting against ransomware and other cyber threats. Establish a consistent backup schedule, such as daily or weekly, to ensure that your most recent data is always secure. Store these backups offline or in a secure, isolated environment to prevent them from being compromised during an attack. In the event of a ransomware attack, having reliable backups allows you to restore your data without paying the ransom, minimizing downtime and financial loss.
2. Patch Management
Ensure all software and systems are up to date with the latest security patches. Cyber attackers often exploit known vulnerabilities, so timely patching can prevent them from gaining a foothold in your network. Regularly updating your systems helps close security gaps that could be exploited by malicious actors, reducing the risk of unauthorized access and potential data breaches. Additionally, implementing automated update mechanisms and monitoring tools can streamline the patch management process, ensuring that no critical updates are missed. By maintaining up-to-date systems, you strengthen your overall security posture and protect your organization from potential threats.
3. Security Awareness Training
Educate your employees about the dangers of phishing emails and other social engineering tactics. Regular training can help them recognize and avoid potential threats.
4. Endpoint Protection
Deploy advanced endpoint protection solutions that can detect and respond to ransomware threats. Look for solutions that offer behavioral analysis, real-time threat intelligence, and automated response capabilities.
5. Network Segmentation
Segment your network to limit the lateral movement of ransomware. By isolating critical systems and data, you can contain the spread of an infection. Network segmentation involves dividing your network into smaller, isolated segments, each with its own security controls. This practice restricts unauthorized access to sensitive areas and limits the ability of ransomware to move laterally across the network.
6. Incident Response Plan
Develop and regularly update an incident response plan. This should include steps for identifying, containing, eradicating, and recovering from a ransomware attack.
The Bottom Line
Eldorado represents a significant threat to both Windows and Linux systems, leveraging advanced techniques to evade detection and maximize its impact. By understanding how Eldorado operates and implementing robust cybersecurity measures, you can better protect your organization from this and other emerging threats. Stay vigilant, stay informed, and stay secure.
Secure your environment with Auxin’s Context Aware Security—Sign up free forever!






