Enhancing Cyber Defense: Best Practices for Implementing DevSecOps
As cyber threats become more complex and regular, the need for integrating security into the development process has never been more pressing. This is where DevSecOps comes into play. DevSecOps, short for Development, Security, and Operations, is an approach that embeds security practices into the DevOps process, assuring that security is a shared responsibility across the entire development lifecycle.
Here are some best practices for implementing DevSecOps to enhance your cyber defense.
Foster a Security-First Culture
The foundation of a successful DevSecOps strategy is a security-first culture. Security should be ingrained in your organization’s processes and mindset. Encourage collaboration between development, security, and operations teams to break down silos and boost a shared responsibility for security. Regular training and understanding programs can help educate your teams about the importance of security and how they can contribute to keeping a secure environment.
Automate Security Processes
Automation is a cornerstone of DevSecOps. By automating security processes, you can ensure consistent and repeatable security checks throughout the development lifecycle. Implement automated security testing tools to scan code for vulnerabilities during the build and deployment phases. This helps identify and address security issues early in the development process, reducing the risk of vulnerabilities in production.
Integrate Security into CI/CD Pipelines
Continuous Integration and Continuous Deployment (CI/CD) pipelines are essential for rapidly delivering software updates. Integrating security into these pipelines ensures that security checks are integral to the development process. Implement static application security testing (SAST) and dynamic application security testing (DAST) tools within your CI/CD pipelines to identify vulnerabilities at various stages of development. This allows for immediate feedback, enabling developers to fix issues promptly.
Implement Robust Access Controls
Effective access control mechanisms are crucial for protecting your development environment. Ensure that only authorized personnel have access to critical systems and sensitive data. Implement the principle of least privilege, granting users the minimum level of access necessary to perform their tasks. Use multi-factor authentication (MFA) to add a layer of security, and regularly review and update access permissions to prevent unauthorized access.
Conduct Regular Security Audits and Assessments
Frequent security audits and assessments are crucial for determining potential vulnerabilities and ensuring compliance with security standards. Conduct periodic code reviews, vulnerability assessments, and penetration testing to identify and mitigate security risks. Use the findings from these assessments to improve your security practices and address any gaps in your DevSecOps processes.
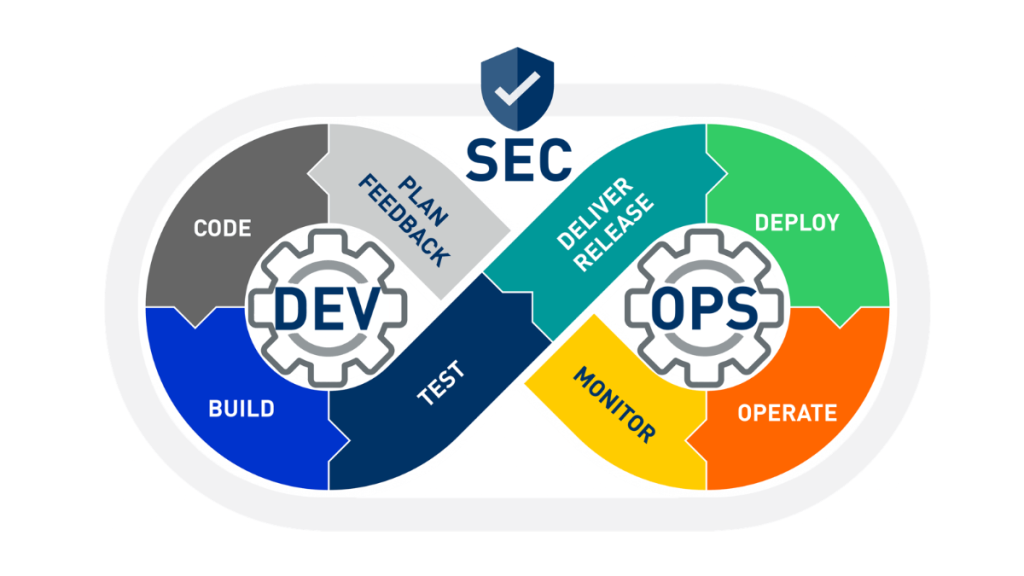
Embrace Shift-Left Security
Shift-left security is integrating security measures early in the development process. By shifting security to the left, you can identify and address vulnerabilities before they become more challenging and costly. Encourage developers to write secure code from the outset and provide them with the necessary tools and resources. Integrate security requirements into your design and planning phases to ensure security is considered.
Leverage Security as Code
Security as Code (SaC) defines security policies and controls as code, which can be versioned, tested, and automated like application code. This approach enables you to apply consistent security policies across your infrastructure and applications. Infrastructure can be used as code (IaC) tools to automate the provisioning and management of secure infrastructure. By treating security as code, you can ensure that security configurations are applied consistently and can be easily updated as needed.
Monitor and Respond to Security Incidents
Effective monitoring and incident response are critical components of a robust DevSecOps strategy. Implement ongoing monitoring to detect and respond to security incidents in real-time. Security report and event management (SIEM) systems collect and analyze security data from various sources. Set an incident response plan that outlines the measures to be taken in the event of a security breach, and regularly test and update this plan to ensure its effectiveness.
Wrapping Up
Implementing DevSecOps is essential for enhancing your organization’s cyber defense in today’s threat landscape. You can build a robust security posture by fostering a security-first culture, automating security processes, integrating security into CI/CD pipelines, and embracing practices such as shift-left security and Security as Code. Regular audits, adequate access controls, and continuous monitoring strengthen your defenses, ensuring your organization can proactively identify and mitigate security risks. Embrace these best practices to create a secure development environment that protects your assets and maintains the trust of your customers.
For more information on enhancing your cybersecurity with DevSecOps, visit Auxin Security.






