Cracking the Code: DAST will improve and fix Vulnerabilities 100%
A Gartner article states that “Dynamic application security testing (DAST) technologies are designed to detect conditions indicative of a security vulnerability in an application in its running state”. DAST is considered black-box testing as the code or application architecture is not exposed to the testing tool. So, it comes into action after SAST because run time issues are not detected and solved at run time. The run time issues are in the spotlight this time. Problems like user authentication and server configuration cannot be dealt with during early developmental stages, so it helps the system deal with such situations.
Majorly, DAST helps when requests, response queries, data injections, session and id management, and authentication issues come up. It deploys a fault injection on the application by inserting multiple malware into the data and making it immune to such activities as cross-site scripting or SQL injections. Side by side, highlighting any loopholes if any, the system has.
Advantages
Web and Application Testing
The best part about AlphaDAST is that code availability or architecture isn’t an issue. Modern applications are complicated; different frameworks for different parts of an application, external libraries, and business logic make detecting some early-stage changes impossible. The only way to approach such systems with full scanning ability is AlphaDAST. AlphaDAST provides a combined application and surface scanning that gives a full 360 view of the application.
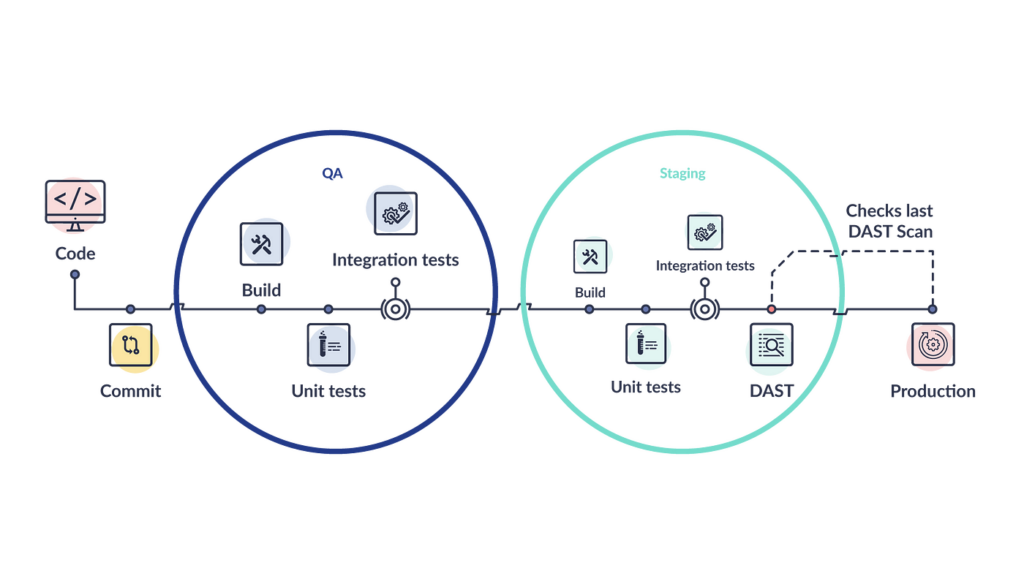
Deployment at Production
Traditionally testing is done in three phases; SAST in developmental stages, DAST at production, and, in the end, manual testing. But just as contemporary it can be incorporated with development-level testing, it can also scan production environments. This new testing phase is an excellent asset for stakeholders because you can quickly gauge live environments and plan accordingly. It is also a common practice to periodically scan existing production deployments to detect any bugs introduced by configuration or check for newly discovered vulnerabilities at any stage.
Modernize Penetration Testing
Dynamic testing emerged when manual testing was tiring and produced slow results. It is still practiced but very late in the SDLC. A tool such as AlphaDAST will automate your SDLC, automate grunt work very efficiently, and display vulnerability alerts. We at AUXIN use context-aware vulnerability scans to deliver ready results, allowing developers to focus on more complex vulnerabilities.
Encryption
Encryption algorithms are the most popular these days against advanced attacks. Encryption has become an industry standard against sensitive information and harmful attackers. Instead of checking the robust encryption algorithm in DAST, the tool tries to break through the loopholes in the encryption technique used and thus test the possible impact on the application. This technology follows the way which is used by a cyber-criminal that is more focused on directly breaching or bypassing the encryption mechanism used.
AlphaDAST
After considering various DAST tools such as Rapid7, Detectify, Invicti, and Intruder, we at AUXIN have launched AlphaDAST. A software best suited for your application security and other security needs. The following criterion summarizes why we are the best at the game.
We use Unauthenticated and authenticated scans that go beyond OWASP10. A significant edge that Auxin has over our competitors is that we allow scans behind a firewall. So, no loophole gets unchecked. To minimize the challenges, AUXIN allows vendor and consultant mode. This will enable stakeholders and company developers to have shared access to the tool so their concerns regarding privacy and confidentiality get resolved. We try out best to minimize false positives as much as we can and provide industry-specific scan and test results. AlphaDAST allows applications to scale more significantly without lowering their security. You can read more about Auxin and our services at auxin.io.






