How to get started with IAC (Infrastructure as code)
What is IAC Security?
Infrastructure as Code (IAC) Security involves implementing security measures and best practices within code-based infrastructure management processes. It encompasses secure coding practices, version control, and auditing for tracking changes and ensuring accountability. Automated testing is integrated into continuous integration and deployment pipelines to identify and rectify vulnerabilities early. Configuration management tools define and deploy infrastructure consistently, while secrets management ensures sensitive information is handled securely. The concept of immutable infrastructure is adopted to minimize configuration drift and enforce a consistent security posture.
Advantages of IAC Security
Infrastructure as Code (IAC) Security offers several benefits that contribute to improved efficiency, reliability, and security in managing infrastructure deployments:
- Consistency: IAC enables consistent deployment and configuration of infrastructure components across environments, reducing the risk of configuration drift and ensuring uniform security policies are applied everywhere.
- Scalability: With IAC, scaling infrastructure becomes more accessible and more efficient as code-based configurations can be easily replicated and modified to accommodate changing workload demands.
- Automation: Automation in IAC streamlines the deployment process, reduces manual errors, and accelerates time-to-market for applications and services while ensuring security measures are consistently applied.
- Version Control and Auditing: Version control systems provide visibility into changes made to infrastructure code, facilitating auditing, collaboration, and rollback capabilities, which are crucial for maintaining security and compliance.
- Security Compliance: IAC Security enables the enforcement of security policies, regulatory compliance requirements, and governance frameworks through automated checks, ensuring that deployed infrastructure meets industry standards and legal obligations.
Check Out This Practical Guide
We’re about to delve into a practical guide on conducting IAC security scans. If you want to utilize AlphaScale for this purpose, sign up using the following link: https://portal.auxin.cloud/signup. Scanning your code is free. If you haven’t registered yet, visit the link and log into your account.
Let’s Begin
Upon logging in, you’ll encounter a display showcasing a range of options. You’ll find AlphaScale, which you’ll click to access. Once selected, you’ll be directed to the AlphaScale dashboard, where you can navigate the available features and functionalities.
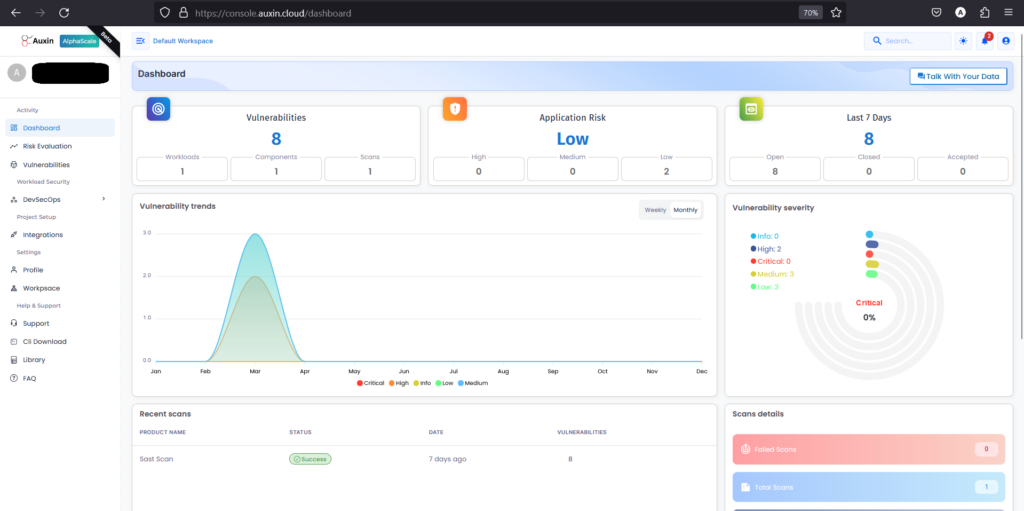
Dashboard
The dashboard is a comprehensive hub, providing insights into vulnerabilities, trends, application risks, and severity levels. Users can quickly assess their applications’ security posture, prioritize actions based on severity, and stay informed about emerging threats. This centralized interface enhances decision-making by presenting crucial data in a digestible format, enabling proactive risk mitigation strategies.
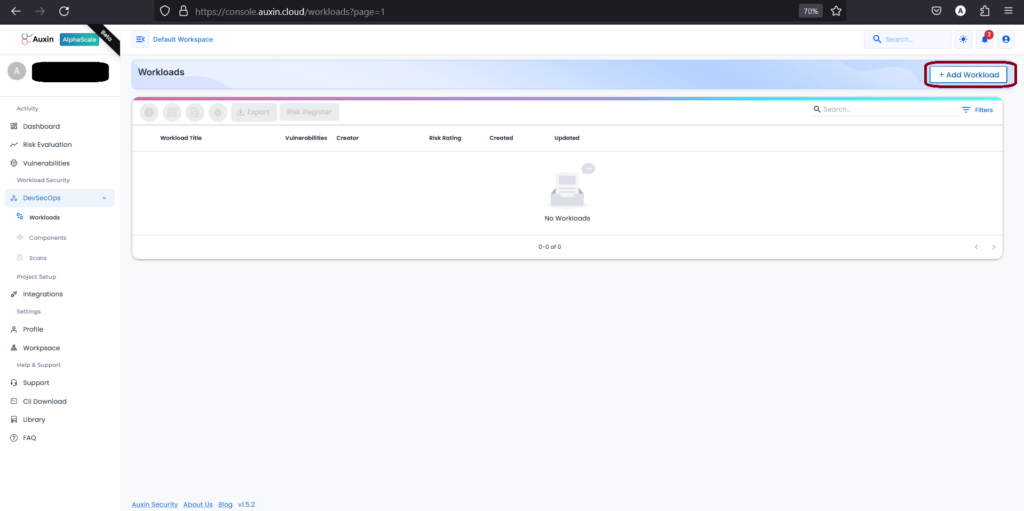
Create Workload:
Creating a workload means teams can systematically organize and manage various components, application risks, and scans. Ultimately, creating a workload fosters a structured and disciplined environment within DevSecOps. Here are the following steps:
Step 1
To create a Workload, navigate to the DevSecOps section and click “Add Workload.” This streamlined process allows users to efficiently allocate resources and manage tasks within their development and security operations.
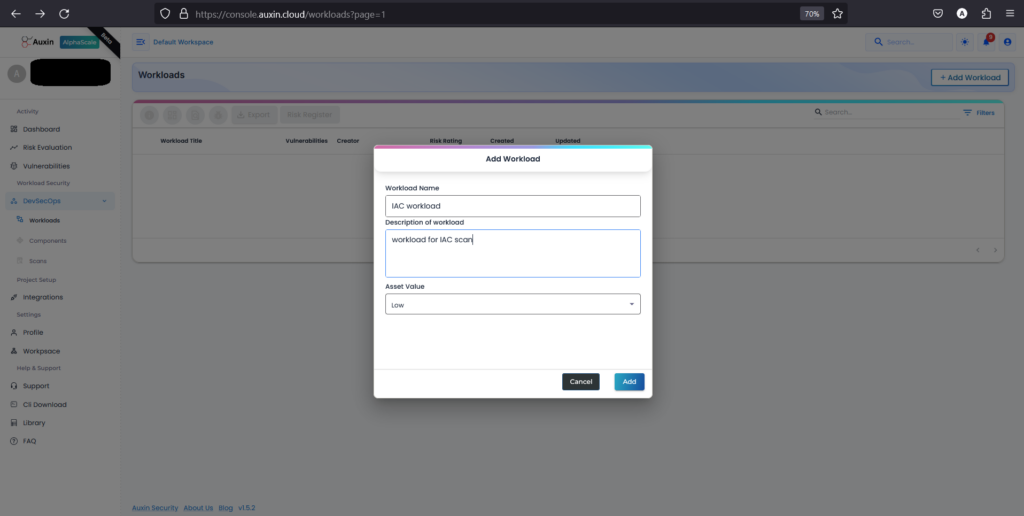
Step 2
Input the desired Workload Name, Description, and Asset Value, then proceed by clicking on the “Add” button. This straightforward process ensures clear identification and categorization of tasks or projects, facilitating effective management and allocation of resources within the workflow.
Create Component:
Creating components within the workload ensures accurate representation and efficient management of scan vulnerabilities, facilitating seamless DevSecOps processes. Here are the following steps:
Step 1
To create a Component, access the designated section and select “Add Component.” This straightforward action enables users to incorporate new elements into their projects or systems efficiently.
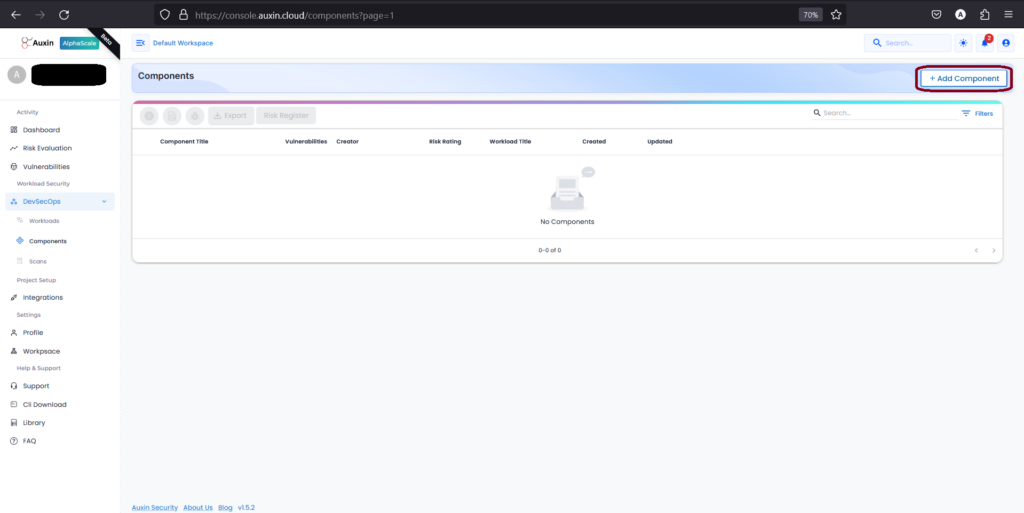
Step 2
Input its Name and Description, then choose the previously created Workload and the designated Asset Value before clicking “Add.” This systematic approach ensures accurate identification and allocation of components within the project framework, facilitating streamlined project management and resource allocation.
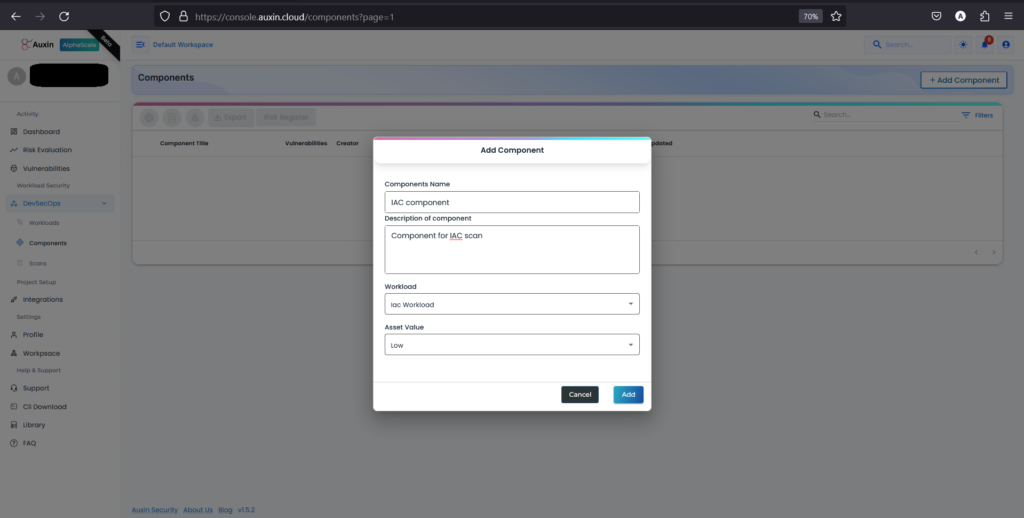
Create Scan:
An IAC scan is to analyze the source code for vulnerabilities systematically. By initiating this scan, developers can identify and rectify security flaws early in the IAC code development process, ensuring a more secure and resilient application upon deployment. Here are the following steps:
Step 1
To initiate a scan, navigate to the Scans section and select “Add Scan.”
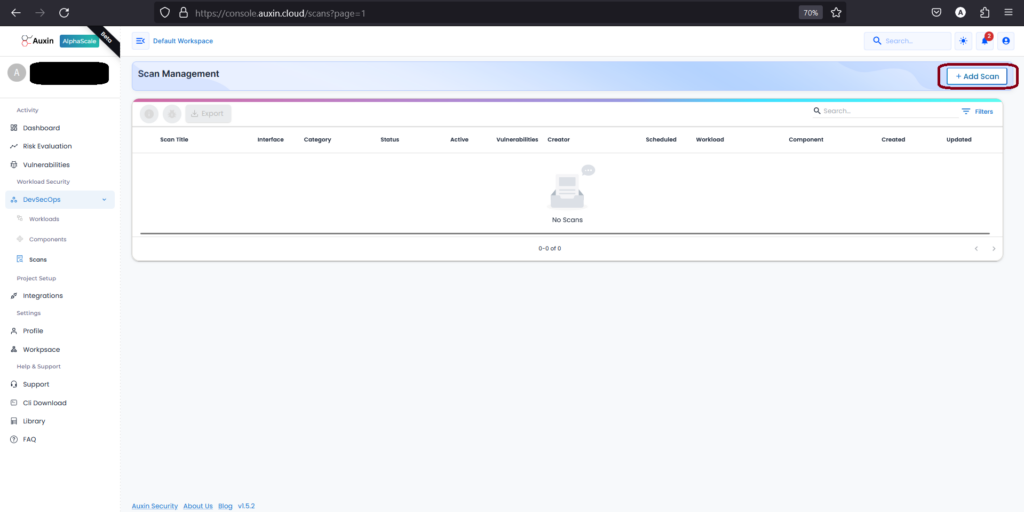
Step 2
Provide a descriptive Scan Name and Description, then choose the previously established Workload and Component. Select the default Agent or specify a preferred one, then proceed by clicking “Next.”
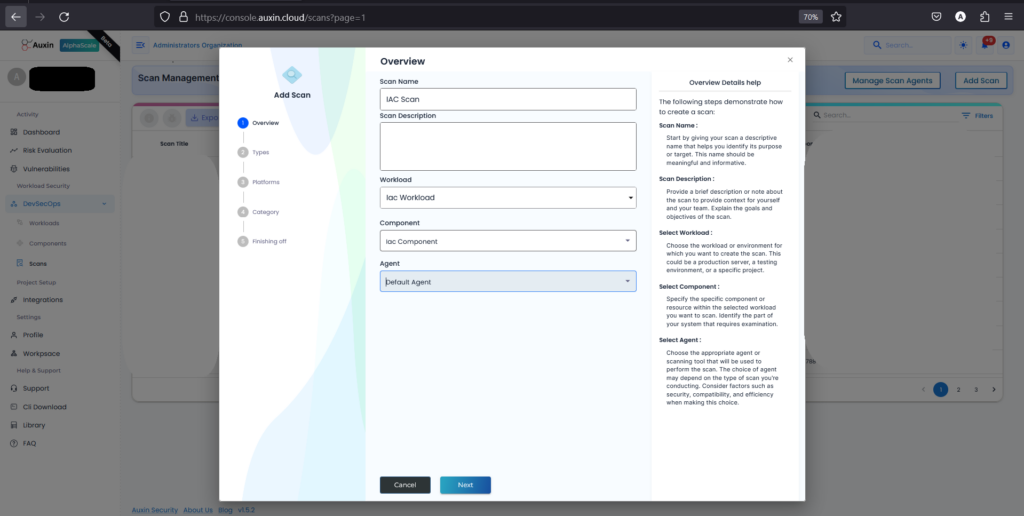
Step 3
Selecting the IAC scan type ensures thorough evaluation of your infrastructure’s code for vulnerabilities. Click ‘Next’ to proceed and fortify your digital assets with proactive security measures aligned with modern best practices.
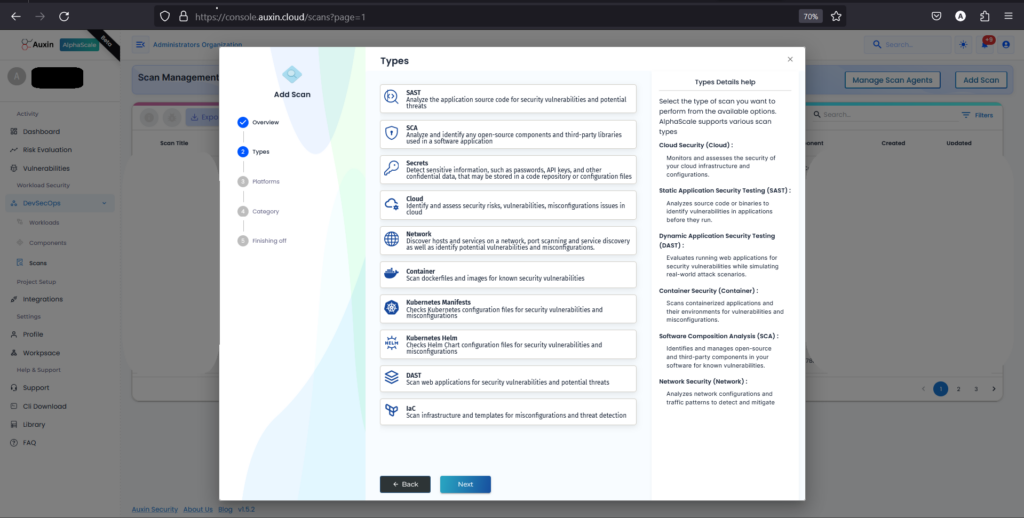
Step 4
After selecting IAC as the scan type, choose the platform where your IAC code resides and proceed by clicking “Next.” This step ensures that the scanning process targets the correct repository or environment where the code is stored, facilitating accurate analysis and detection of security vulnerabilities.
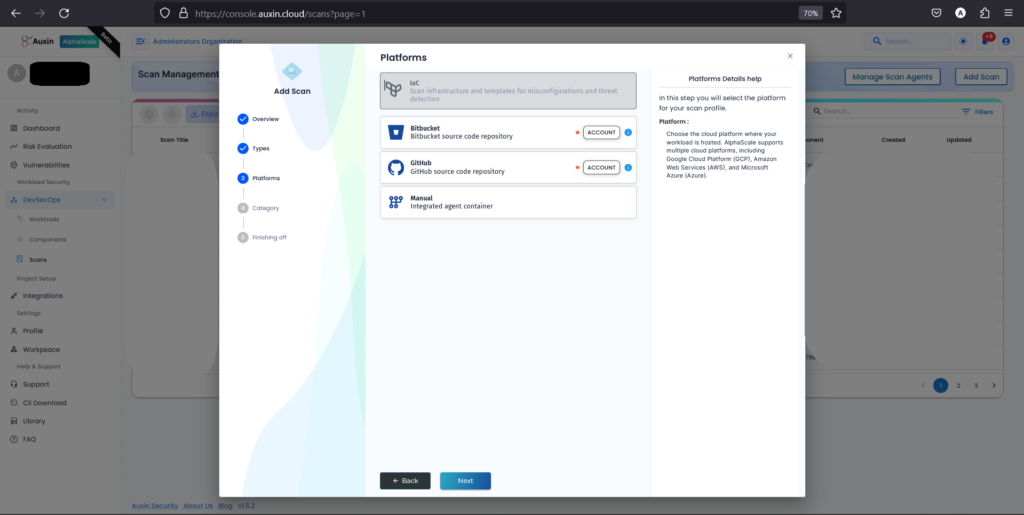
Step 5
After choosing GitHub as the platform for IAC code, select “Private” to indicate that the repository is not publicly accessible, then proceed by clicking “Next.” This ensures that the scanning process can access and analyze the code stored in your private GitHub repository securely.
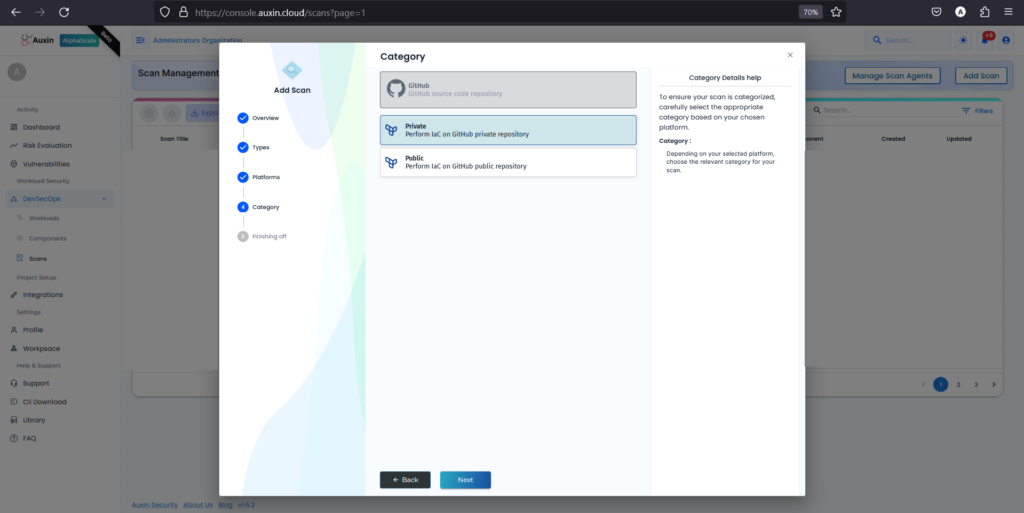
Step 6
Enter the Branch Name corresponding to the branch of your code repository you want to scan, then provide the Token for authentication and the private repository URL. After ensuring the accuracy of the provided information, click on “Run Scan” to initiate the scanning process.
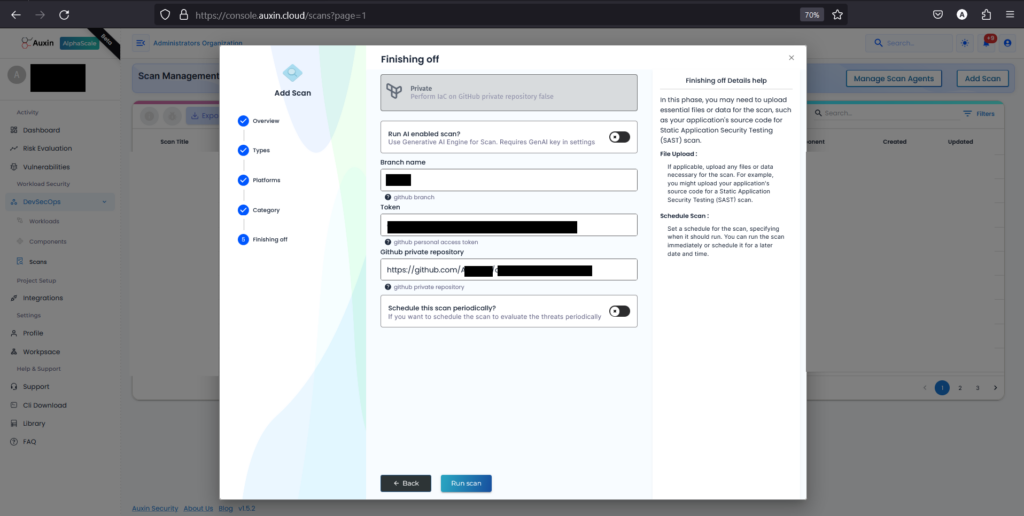
Step 7
Upon completion of the scan, review the generated report to identify vulnerabilities within your IAC code. This comprehensive analysis provides insights into potential security risks, enabling you to prioritize and address issues effectively.
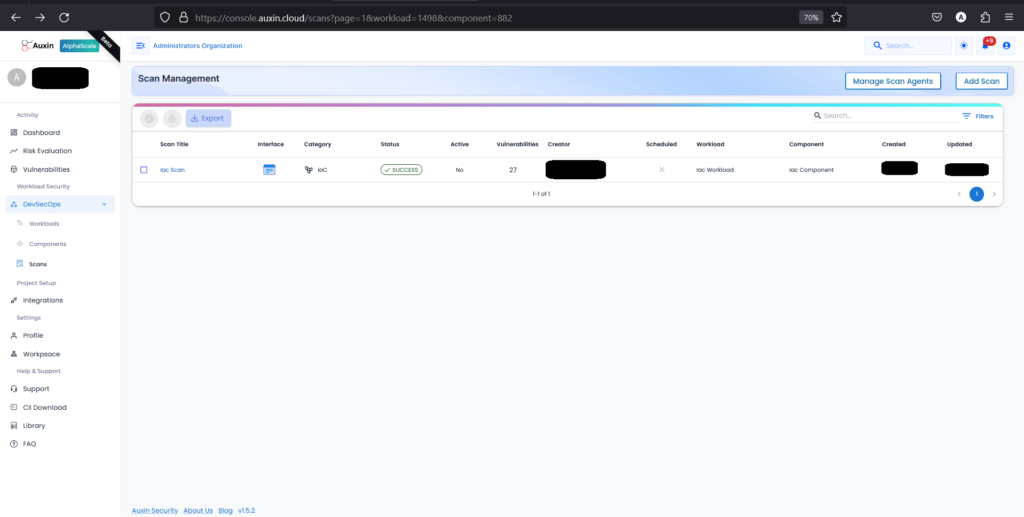
Step 8
To review IAC scan results, access the scan management dashboard, locate your scan title, and click to Scan title report. Identify vulnerabilities by severity, prioritize fixes, and collaborate with teams to address security risks efficiently.
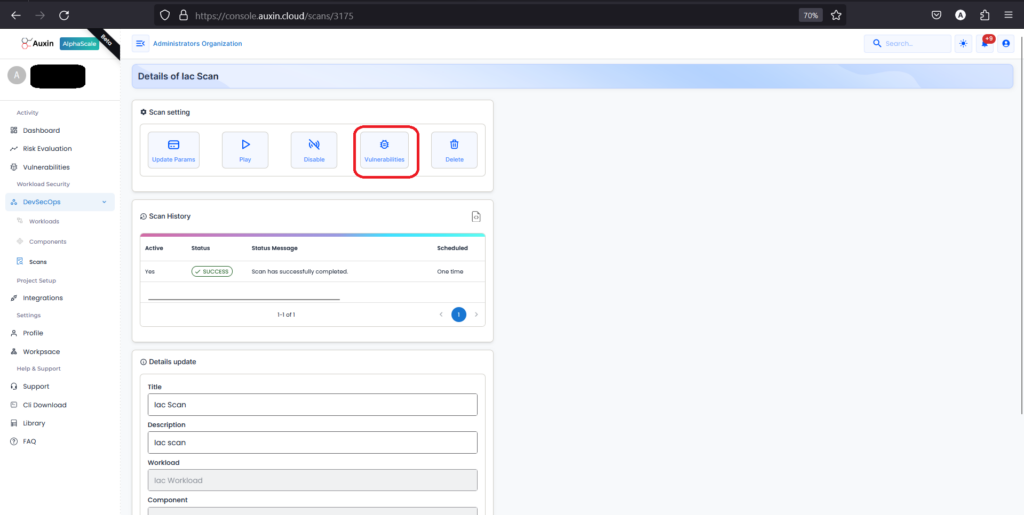
Step 9
Next, within the details of your IAC scan, locate and click on the option specifically labeled “Vulnerabilities” to access a comprehensive list of the security issues detected during the scan.
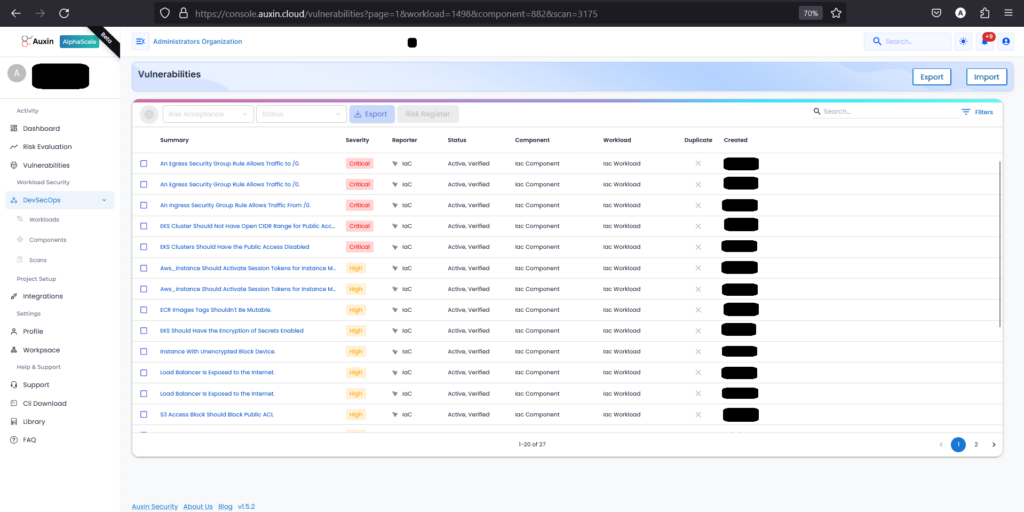
After identifying vulnerabilities in your IAC code, you can export or import them for further analysis or integration with other tools.
Next Steps: Prioritizing and Addressing Vulnerabilities
Review Findings: Carefully analyze the vulnerabilities identified by the IAC scan. For each vulnerability, assess the severity level (critical, high, medium, low) and the potential impact on your application. In line with our example, the finding “An Egress Security Group Rule Allows Traffic to /0” indicates that an outbound rule in a security group allows unrestricted traffic to all IP addresses, potentially posing a security risk.
Prioritize Risks: First, address the most critical, then high, medium, and last one, which is low vulnerabilities. These vulnerabilities pose the most significant security risk and warrant immediate attention. In line with our example, to prioritize the critical vulnerability of an egress security group rule allowing traffic to /0, consider its potential impact, compliance implications, attack vectors, existing mitigations, business impact, stakeholder input, create a remediation plan, and monitor effectiveness post-implementation.
Remediation Steps: Develop a plan to fix the identified vulnerabilities. This may involve identifying security groups and modifying egress rules. In line with our example, The remediation steps for the vulnerability of an egress security group rule allowing traffic to /0 include:
- Identify the specific security group and rule allowing traffic to /0.
- Modify the egress rule to restrict outbound traffic to specific IP addresses, subnets, or security groups as per your security policies and requirements.
- Test the modified rule to ensure it does not impact normal application functionality.
- Monitor the security group’s traffic logs to verify that the new egress rule restricts traffic to authorized destinations.
- Implement regular audits and reviews of security group configurations to detect and address similar vulnerabilities in the future.
Verification and Retesting: Once a vulnerability has been addressed, retest the IAC code to ensure the fix is effective. This iterative process guarantees that your application remains secure. In line with our example, these steps are implemented to verify and retest the vulnerability.
- Verify Remediation Implementation: Verify that the fix has been correctly applied according to the outlined steps.
- Unit Testing: Conduct unit and integration tests to ensure proper functionality and interaction with other components.
- Security Scans: Run scans to detect whether Egress rules are implemented correctly or not.
By incorporating this additional step, you’ll establish a clear action plan for resolving vulnerabilities and securing an IAC code.
How can Auxin help you with DAST?
With Auxin, you can automate application security testing, access comprehensive security reports, and address application defects proactively before deployment. Our proficient security experts conduct vulnerability testing according to industry best practices, utilizing a range of security testing tools and proprietary vulnerability scanners to ensure thorough assessment at every application layer. Let’s get in touch with Auxin: https://auxin.io/contact-us/.
Wrapping Up
Infrastructure as Code (IAC) Security is paramount for ensuring the robustness and resilience of modern IT infrastructures. Organizations can mitigate potential threats by integrating security measures into code-based infrastructure management processes. Prioritizing tasks such as vulnerability scanning, risk assessment, and remediation is essential for maintaining compliance standards and safeguarding against emerging threats. Utilizing tools and platforms for IAC security streamlines the process, offering features for conducting scans and facilitating remediation efforts. Through systematic review, prioritization, and remediation of vulnerabilities, organizations can fortify their defenses and foster a culture of security within DevSecOps practices, ensuring the reliability and integrity of their infrastructure deployments.






