How Russian Hackers Infiltrated Microsoft
On March 8th, 2024, Microsoft made a shocking revelation: it had become the target of a cyberattack orchestrated by a state-sponsored Russian hacking group known as Midnight Blizzard. This breach, involving the unauthorized access and exfiltration of critical source code repositories, sent shockwaves through the tech industry, raising significant concerns about the security of one of the world’s largest technology companies and the potential impact on its vast user base. This blog delves into the intricacies of the attack, its implications for Microsoft and beyond, and the urgent need for heightened cybersecurity measures in an increasingly digital world.
Here’s What We Know
In a stunning revelation, Microsoft announced on March 8th, 2024, that it had fallen victim to a cyberattack orchestrated by a state-sponsored Russian hacking group known as Midnight Blizzard, also identified as APT29 or Cozy Bear. The breach involved the unauthorized access and exfiltration of source code repositories, raising concerns about the potential implications for one of the world’s largest technology companies and its vast user base.
Timeline of Events
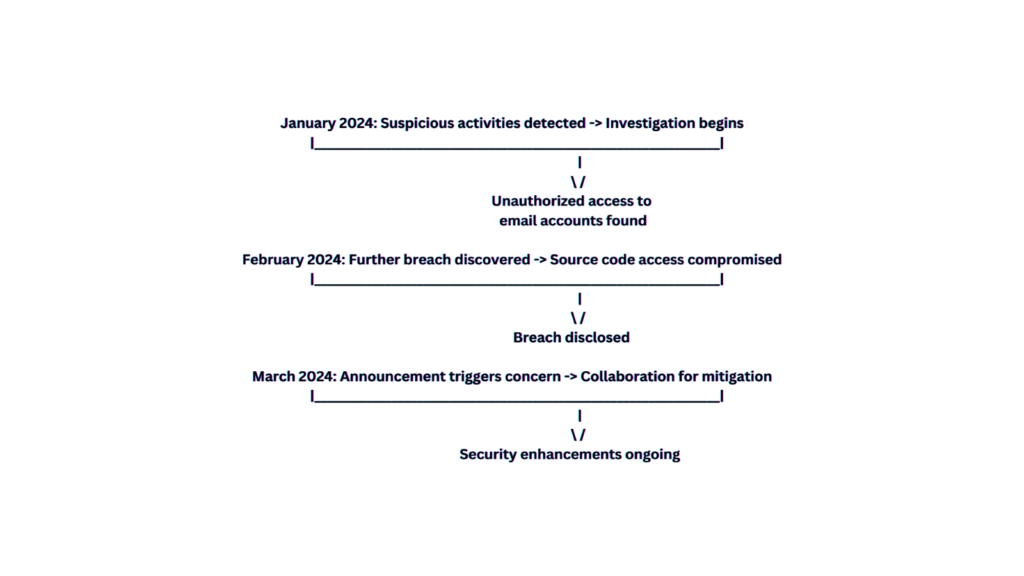
As per The Verge this disclosure comes in the wake of an earlier detection in January 2024, when Microsoft first observed suspicious activities within its corporate network. At that time, the intrusion was limited to unauthorized access to employee email accounts, which prompted an immediate investigation. However, the subsequent findings have unveiled a far more severe breach, with Midnight Blizzard penetrating deeper into Microsoft’s infrastructure and gaining access to valuable source code repositories.
Midnight Blizzard: A Formidable Adversary
Midnight Blizzard, a notorious cyber-espionage group believed to have ties to the Russian government, has been implicated in several high-profile cyberattacks targeting governments, corporations, and critical infrastructure worldwide. Their sophisticated tactics and advanced capabilities have made them a formidable adversary in the realm of cybersecurity, capable of exploiting vulnerabilities and circumventing traditional defense mechanisms.
“According to Tenable CEO Amit Yoran in a statement shared with The Hacker News, the breach of Microsoft by Midnight Blizzard is a big problem. Midnight Blizzard is not just a small group of criminals; they’re a well-organized team supported by Russia. They know exactly how valuable the data they’ve stolen is and how to cause the most damage with it.”
The theft of source code is particularly alarming due to the potential repercussions it could have on Microsoft’s products and services. Source code serves as the blueprint for software development, containing proprietary algorithms, protocols, and other intellectual property crucial to the functionality and security of Microsoft’s vast array of products, including Windows, Office, and Azure.
Microsoft’s Response
While Microsoft has assured its customers that there is currently no evidence of any impact on its products or services resulting from the breach, the incident underscores the persistent threat posed by state-sponsored cyber-espionage groups and the critical importance of robust cybersecurity measures.
In response to the breach, Microsoft has taken immediate steps to contain the incident, enhance its security protocols, and collaborate with law enforcement agencies and cybersecurity experts to investigate the full extent of the breach and identify any potential vulnerabilities that may have been exploited.
What’s Next?
Microsoft is actively investigating the attack and working to bolster its security measures. They’ve urged customers to remain vigilant and implement strong password protocols.

Auxin’s Recommendations for Enhanced Cybersecurity
According to Auxin’s experts, building a resilient security posture is essential in today’s digital landscape, where cyber threats continue to evolve in sophistication and scale. By implementing these recommendations, organizations can bolster their cybersecurity defenses and reduce the likelihood of falling victim to cyberattacks like the one experienced by Microsoft.
- Implement Multi-Factor Authentication (MFA): Enforce multi-factor authentication across all user accounts to add an extra layer of security, making it significantly harder for unauthorized individuals to gain access, even if credentials are compromised.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to proactively identify address vulnerabilities within your systems and networks. This proactive approach can help uncover weaknesses before they can be exploited by malicious actors.
- Enhance Monitoring and Detection Systems: Invest in advanced monitoring and detection systems capable of identifying suspicious activities and potential breaches in real-time. Early detection can significantly reduce the impact of a cyberattack by enabling swift response and containment.
- Regular Software Updates and Patch Management: Stay vigilant about applying software updates and patches promptly. Many cyberattacks exploit known vulnerabilities for which patches have already been released. By keeping your systems up to date, you can mitigate the risk of falling victim to such attacks.
- Backup and Disaster Recovery Plans: As per Gartner implement robust backup and disaster recovery plans to ensure that critical data can be quickly restored in the event of a breach or system failure. Regularly test these plans to verify their effectiveness and readiness.






